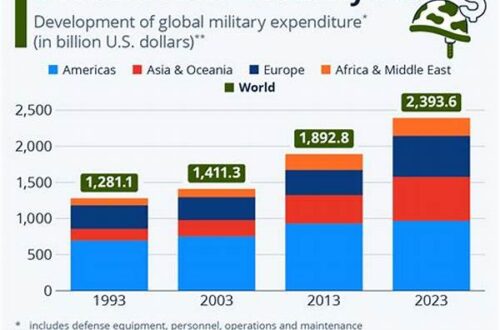
In an era where data breaches and cyber threats are increasingly prevalent, organizations are tasked with the critical responsibility of securing sensitive information. One of the most significant vulnerabilities arises from within—the insider threat. To mitigate this risk, the development of a structured insider threat program is paramount. This initiative not only fortifies security measures but also cultivates a culture of vigilance and responsibility among employees.
Understanding Insider Threat Program Development
The process of insider threat program development requires meticulous planning and execution. It begins with a comprehensive risk assessment, identifying potential threats and vulnerabilities within the organization. Understanding the behaviors and motivations of potential insider threats is crucial. This understanding informs the design of monitoring systems and security protocols that can effectively detect and prevent malicious activities. Furthermore, successful insider threat program development necessitates a balance between robust security measures and respecting employee privacy. This balance is achieved through transparent communication and a clear articulation of the program’s objectives.
Education and training form a foundational element of insider threat program development. Employees must be well-informed about security policies and the implications of insider threats. Regular training sessions and awareness campaigns are instrumental in reinforcing a proactive security culture. In conjunction with these measures, organizations should implement advanced technological solutions such as behavior analytics and threat detection systems to identify and neutralize potential threats. By fostering a collaborative environment where employees are encouraged to report suspicious activities, the insider threat program development process becomes a collective effort towards safeguarding the organization.
Key Components of an Insider Threat Program
One essential component of insider threat program development is establishing a dedicated team to oversee and manage the program.
Another critical aspect is the integration of technological tools that facilitate real-time monitoring and analysis of user behavior.
Policy formulation is a pivotal step in insider threat program development, ensuring that guidelines are clear and enforceable.
Risk assessment and management are integral to insider threat program development, providing a foundation for identifying and mitigating potential threats.
Finally, continuous evaluation and improvement are vital for ensuring the effectiveness of an insider threat program development process.
The Importance of Employee Engagement
In the realm of insider threat program development, employee engagement plays a vital role. Establishing an open line of communication between management and employees is essential. This communication fosters a sense of security and trust within the workplace, encouraging employees to adhere to security protocols and report suspicious activities. The development of an insider threat program is not solely the responsibility of the security or IT departments; it is an organization-wide initiative that involves collaboration across various departments.
Moreover, investing in employee education as part of the insider threat program development is indispensable. Training sessions that educate employees about the implications of insider threats and the importance of adhering to security measures are crucial. Through these initiatives, organizations can create a culture where employees are not only aware of potential threats but are also motivated to be a part of the solution. By aligning organizational goals with security objectives, insider threat program development can transform potential vulnerabilities into strengths, reinforcing the organization’s overall security posture.
Strategies for Insider Threat Mitigation
Various strategies are pivotal in the process of insider threat program development. Establishing a baseline of normal employee behavior is one such strategy.
Implementing strict access controls is crucial in limiting the potential for insider threats.
Ensuring effective user activity monitoring is a core component of insider threat program development.
Developing a strong incident response plan is integral for addressing any detected threats promptly.
Fostering a culture of security awareness reinforces the principles of an insider threat program development effort.
Implementing robust data protection techniques safeguards sensitive information from being compromised.
Regular audits and reviews ensure compliance with risk management policies within insider threat program development.
Incorporating psychological evaluations can provide insights into potential insider threats.
Engaging third-party assessments can offer an impartial view of the program’s effectiveness.
Finally, the utilization of machine learning and artificial intelligence in monitoring activities can enhance the program’s capability.
Challenges and Solutions in Program Development
While the development of an insider threat program is indispensable, it is not without its challenges. One of the primary obstacles is balancing security measures with employee privacy and trust. Overly intrusive monitoring systems can lead to a culture of mistrust and anxiety among employees. To address this, transparency in communication and clear explanations of the necessity and scope of monitoring activities are essential.
Another challenge lies in maintaining up-to-date threat intelligence and technological capabilities. As the cyber threat landscape evolves, so too must the strategies employed in insider threat program development. Regular training for security personnel on the latest developments and technologies is essential in mitigating evolving threats. Additionally, fostering partnerships with industry experts and leveraging external resources can provide further insights and solutions, enhancing the program’s effectiveness and adaptability.
Future Trends in Insider Threat Program Development
As the digital landscape evolves, so too will the strategies and technologies employed in insider threat program development. Artificial intelligence and machine learning are anticipated to play increasingly prominent roles, offering enhanced capabilities in behavior analysis and threat detection. These technologies enable organizations to proactively identify and respond to potential threats, significantly reducing the risk of insider attacks.
Moreover, the integration of machine learning into insider threat program development will facilitate more refined analysis of user behaviors, enabling the detection of anomalies that might indicate potential threats. As these technologies advance, the implementation of predictive analytics will allow for more precise forecasting and proactive measures. Consequently, organizations must remain abreast of technological advancements to ensure their insider threat programs are equipped to meet emerging challenges and threats in the digital realm.
Conclusion: The Path Forward
In summary, insider threat program development is an essential component in modern organizational security strategies. By structuring a comprehensive program, organizations can effectively mitigate the risks posed by insider threats. This development process encompasses not only the deployment of advanced technological solutions but also the cultivation of a security-conscious organizational culture. The success of insider threat program development relies heavily on the active engagement of both management and employees.
Organizations must prioritize ongoing evaluation and adaptation of their programs to address evolving threats. By fostering a proactive security culture that encourages vigilance and accountability, they can safeguard sensitive data and maintain a robust security posture. Through continued investment in technology, training, and strategic planning, insider threat program development will remain a cornerstone of effective corporate governance and risk management in the future.