The contemporary landscape of global security is fraught with complexities, owing in no small part to the persistent and evolving menace of espionage. Governments and corporations alike are increasingly aware of the need for robust mechanisms to safeguard sensitive information. In this context, espionage threat mitigation strategies have emerged as pivotal components of national and corporate security paradigms. These strategies are designed to anticipate, identify, and neutralize the varied tactics employed by foreign intelligence and industrial spies.
Assessing the Espionage Threat Landscape
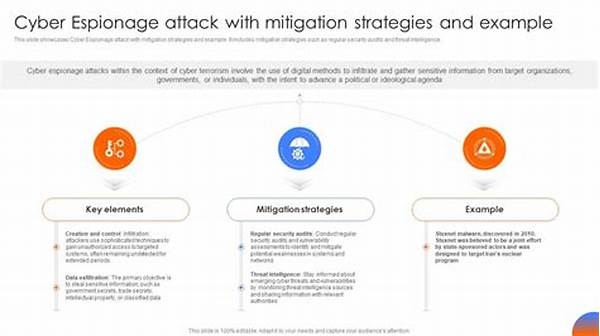
Espionage threat mitigation strategies begin with a comprehensive assessment of potential threats. This phase involves identifying the actors most likely to engage in espionage against a specific entity, whether these be nation-states, competitors, or cybercriminal syndicates. Equally crucial is an understanding of their methods—do they employ cyber intrusion, human intelligence (HUMINT) operatives, or advanced surveillance technologies? By discerning these patterns, organizations can prioritize their vulnerabilities and allocate resources more effectively. The success of espionage threat mitigation strategies thus hinges on a systematic appraisal of threats, enabling proactive defense mechanisms.
Furthermore, this evaluative stage is not a one-off exercise but a continuous process, evolving as the threat landscape shifts. Regular updates to threat assessments ensure that espionage threat mitigation strategies remain aligned with current realities. Strategic foresight, in this manner, is vital in preemptively countering espionage operations, thereby safeguarding critical information assets from compromise.
Implementing Advanced Security Protocols
1. Utilization of Technology: The implementation of sophisticated cybersecurity systems is a cornerstone of espionage threat mitigation strategies, protecting digital assets from unauthorized access.
2. Employee Training Programs: Regular training in recognizing espionage activities ensures that all personnel are equipped to act as first lines of defense against espionage threats.
3. Access Control Measures: Stringent access protocols ensure that only authorized personnel have visibility into sensitive information, thereby reducing vulnerability.
4. Contingency Planning: Developing comprehensive response plans for espionage incidents is a critical component of espionage threat mitigation strategies, ensuring preparedness for potential breaches.
5. Collaboration with Intelligence Agencies: Partnering with national intelligence bodies enhances information sharing, bolstering espionage threat mitigation strategies with external insights and resources.
The Role of Policy in Espionage Threat Mitigation
National and organizational policies form the backbone of espionage threat mitigation strategies. These policies dictate the standards and procedures for securing information against espionage. At the national level, legislative frameworks provide the legal mechanisms to prosecute espionage activities, thereby acting as a deterrent. Internationally, diplomatic engagements can address espionage-related disputes, promoting broader security cooperation among nations.
In corporate realms, internal policies articulate the acceptable use of company resources, confidentiality agreements, and breach protocols. Companies must also comply with relevant national and international regulations, aligning their espionage threat mitigation strategies with legal requirements to mitigate risk. As such, a policy-driven approach ensures a cohesive and enforceable framework for counterespionage practices, integral to safeguarding interests.
Technology and Innovation in Espionage Prevention
Advancements in technology play a significant role in shaping effective espionage threat mitigation strategies. Artificial intelligence and machine learning offer new horizons for detecting and countering espionage attempts. These technologies enable the predictive analysis of potential threats by parsing through vast datasets to identify indicative patterns of espionage activities. Moreover, encryption technologies provide robust protection of data at rest and in transit, ensuring that even if intercepted, sensitive information remains inaccessible to adversaries.
Innovations in surveillance and access control systems further reinforce espionage threat mitigation strategies by enhancing real-time monitoring and swift incident response. Biometric access controls, for instance, ensure that only verified individuals can access restricted areas or information, thereby narrowing opportunities for espionage. The integration of cutting-edge technologies into traditional security architectures thus enhances the efficacy of espionage threat mitigation strategies, creating a resilient defense against espionage.
Espionage Threat Mitigation in Corporate Culture
The role of corporate culture in espionage threat mitigation strategies is indispensable. Cultivating a culture of security awareness among employees embeds espionage prevention into the everyday operations of an organization. Initiatives such as security briefings, workshops, and clear communication channels for reporting suspicious activities foster an environment where vigilance against espionage is second nature.
Furthermore, leadership commitment is crucial in setting the tone for an organizational focus on security. By prioritizing security at the highest levels, organizations can ensure that espionage threat mitigation strategies receive the requisite attention and resources, transforming them from reactive measures to proactive safeguards. A culture of security, therefore, not only deters potential espionages but also strengthens the overall resilience of an organization.
Strategic Partnerships in Espionage Threat Mitigation
The formation of strategic alliances is a vital element of comprehensive espionage threat mitigation strategies. Partnerships with industry peers, government agencies, and security experts facilitate the sharing of intelligence and best practices. These collaborative efforts expand the knowledge base, providing insights into emerging espionage tactics and pooled resources to counter threats more effectively.
Engaging with multilateral forums also offers platforms for broader dialogue and coordinated action against espionage, reinforcing regional and global security. Structured collaboration nurtures trust and builds a community capable of addressing espionage threats through collective vigilance and action. In this manner, strategic partnerships enrich espionage threat mitigation strategies, ensuring they remain robust and responsive to evolving challenges.
Conclusion
In summary, espionage threat mitigation strategies are critical for preserving the integrity and confidentiality of sensitive information in both national and corporate domains. These strategies encompass a wide range of measures, including threat assessment, policy formulation, technological integration, and cultural adaptation. Regular reassessment and adaptation to the changing threat landscape ensure these strategies remain effective and relevant.
Moreover, the success of espionage threat mitigation strategies is bolstered by strategic partnerships and collaborative frameworks that offer shared insights and resources to counteract espionage activities. As such, a holistic approach that combines proactive threat recognition, advanced security protocols, and a culture of vigilance is imperative to mitigate espionage threats effectively, safeguarding invaluable assets against compromise.