In today’s digital age, organizations face myriad challenges in safeguarding their sensitive information. One of the most concerning issues is the insider threat, where employees or contractors misuse their access to compromise the integrity, availability, or confidentiality of enterprises’ valuable data resources. Detecting insider threat activities has emerged as a crucial aspect of cybersecurity strategies, aiming to minimize risks associated with trusted individuals who might intentionally or unintentionally harm an organization. Developing effective mechanisms for monitoring and identifying potential threats within an organization is imperative for maintaining robust security postures and ensuring operational continuity.
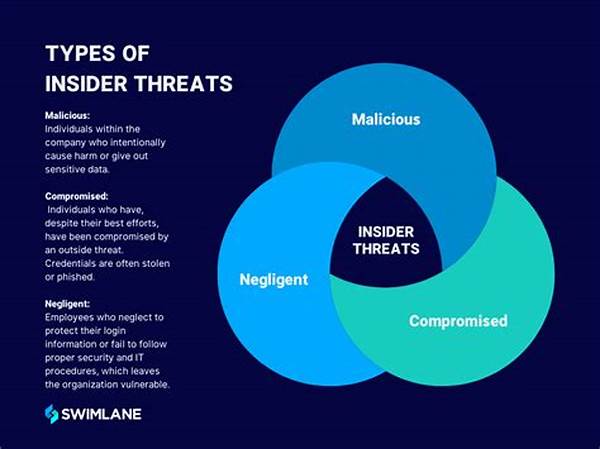
Understanding Insider Threats
Insider threats can manifest through various actions, often driven by malicious intent, negligence, or external pressure. Detecting insider threat activities requires an intricate understanding of organizational behavior, alongside advanced monitoring techniques. Organizations must balance vigilance with respect for employee privacy, fostering an environment where trust is not compromised. Implementing a proactive approach through behavioral analytics, machine learning, and anomaly detection tools empowers organizations to identify deviations from normal activities, thereby enhancing their capability to intercept potential threats before they materialize into substantial harm.
Technological advancements play a crucial role in detecting insider threat activities effectively. Asset monitoring, access control systems, and data loss prevention software are pivotal in identifying unusual patterns indicative of insider meddling. However, technology alone is insufficient; addressing insider threats necessitates a comprehensive strategy encompassing policies, employee education, and a culture of transparency. Regular training sessions and workshops are essential in educating personnel about security protocols, emphasizing the significance of vigilance, ethical conduct, and adherence to organizational policies. By fostering awareness and accountability, organizations can mitigate the risks associated with insider threats.
Identifying Anomalous Behaviors
1. An integral part of detecting insider threat activities is identifying anomalous behaviors that deviate from established baselines. By correlating user activities, organizations can discern potential threats, enabling timely intervention.
2. Implementing robust monitoring systems is essential in detecting insider threat activities. These systems track user actions, flag inconsistencies, and generate alerts for suspicious activities, facilitating early detection and response.
3. Comprehensive training programs are instrumental in detecting insider threat activities. By educating employees on recognizing potential threats, organizations can diminish vulnerabilities and cultivate a vigilant workforce.
4. The integration of artificial intelligence in detecting insider threat activities has significantly improved the precision and efficiency of identifying potential threats, thus aiding in proactively managing risks.
5. Strong access controls and regular audits are vital in detecting insider threat activities. Restricting access based on role requirements minimizes exposure and ensures that only authorized personnel can access sensitive data.
Technological Interventions in Threat Detection
In the contemporary cybersecurity landscape, leveraging technology is paramount in detecting insider threat activities. Advanced tools such as user behavior analytics (UBA) and security information and event management (SIEM) systems provide a critical layer of defense by analyzing vast datasets to detect deviations indicative of malicious activities. By correlating multiple data points, these technologies enhance the ability to identify patterns that might otherwise remain unnoticed. Consequently, organizations are equipped to respond swiftly to emerging threats, thus safeguarding their digital resources.
Moreover, the application of artificial intelligence and machine learning in detecting insider threat activities has marked a significant evolution in threat detection capabilities. These technologies enable real-time analysis and evaluation of user actions, thereby facilitating the identification of nuanced threats that traditional methods might overlook. As organizations continue to invest in technology-driven solutions, the assurance of data security and integrity becomes increasingly attainable, fortifying defenses against potential insider threats.
Innovating Security Protocols
To effectively combat the menace of insider threats, organizations must innovate and refine their security protocols continuously. Detecting insider threat activities is not solely dependent on technology but also on cultivating a culture of security awareness. Integrating security as a core component of organizational ethos ensures that employees are aware of potential threats and their roles in mitigating them. This proactive stance not only reinforces trust but also aligns with compliance and regulatory mandates, which are crucial in upholding a comprehensive security framework.
Moreover, fostering a secure digital ecosystem by regularly updating security policies and protocols is fundamental in detecting insider threat activities. Clear guidelines tailored to the organization’s unique risk profile assist in preventing unauthorized access and maintaining data integrity. Engaging employees in dialogues about security threats and best practices promotes a participative approach to security, thereby fostering a collaborative environment where security is a shared responsibility. By embedding security into the organizational culture, companies stand a better chance of mitigating insider threats.
Human Element in Threat Detection
Despite technological advancements, the human element remains central to detecting insider threat activities. Employees are both the first line of defense and the potential source of threats. Therefore, investing in employee education and fostering a security-conscious culture is imperative. Routine training sessions that emphasize ethical behavior, data protection policies, and threat awareness are crucial in shaping a workforce capable of identifying and responding to potential security breaches swiftly and effectively.
Engaging employees in regular security evaluations and feedback sessions also enriches the threat detection process, ensuring policies remain adaptable to emerging trends and challenges. Moreover, cultivating an organizational culture that values transparency and communication facilitates early detection of insider threats, as employees are more likely to report suspicious behavior when they feel empowered and trusted. By harnessing the human element, organizations can create a formidable defense against insider threats.
The Future of Insider Threat Management
The landscape of insider threat management is continuously evolving, with organizations deploying innovative strategies to safeguard their assets. Detecting insider threat activities will increasingly rely on a synthesis of technological prowess and organizational culture, both of which are indispensable in ensuring robust security frameworks. As cybersecurity threats become more sophisticated, organizations must remain vigilant, adapting to new challenges through ongoing education, policy refinement, and technology adoption.
Future strategies will likely emphasize predictive analytics, enabling organizations to preemptively identify and neutralize potential threats. Investment in emerging technologies, coupled with fostering a resilient organizational culture, will serve as the foundation for detecting insider threat activities. By prioritizing a holistic approach, organizations position themselves to not only react to threats effectively but also anticipate and mitigate potential risks, securing their long-term operational integrity.
Conclusion
In summation, detecting insider threat activities is imperative in maintaining the integrity and security of organizational assets. This endeavor necessitates the confluence of advanced technology, robust policies, and a culture of awareness. As organizations navigate the complexities of the digital age, they must integrate comprehensive strategies that address both technological and human vulnerabilities to protect against insider threats effectively. Fostering a security-conscious environment where employees are educated and vigilant, paired with leveraging innovative technologies, will ensure organizations are well-positioned to detect, deter, and defend against insider threats, securing their valuable resources and maintaining trust within and outside the organization.