In the contemporary digital landscape, organizations face a myriad of challenges related to data security. One prominent issue is the occurrence of data breaches, which can result in significant financial, legal, and reputational damage. As breaches become increasingly sophisticated, it is crucial for organizations to develop and implement effective data breach response strategies. These strategies serve as comprehensive frameworks that guide businesses in mitigating risks and minimizing the impact of breaches. A well-structured response strategy not only safeguards sensitive information but also ensures regulatory compliance and builds trust with stakeholders.
Importance of Data Breach Response Strategies
A robust data breach response strategy is essential for organizations aiming to protect their digital assets and maintain their reputation in the market. These strategies encompass a series of actions designed to promptly detect, respond to, and mitigate the effects of data breaches. Initially, it is imperative to establish a reliable detection mechanism that can identify breaches at the earliest possible stage. This involves employing advanced technologies and monitoring tools that can swiftly signal any anomaly or unauthorized access to sensitive data.
Once a breach is identified, the next critical step in data breach response strategies involves containing the breach to prevent further data exfiltration. This may require the isolation of affected systems or networks and the engagement of cybersecurity experts to assess the severity of the breach. Communication plays a pivotal role during this phase, as timely and transparent notifications to stakeholders, including affected individuals and regulatory bodies, are essential to maintaining trust and fulfilling legal obligations.
After containment, a thorough investigation is necessary to understand the root cause of the breach and implement corrective measures. This involves reviewing system logs, conducting forensic analyses, and revisiting security protocols to ensure vulnerabilities are addressed. Furthermore, data breach response strategies should encompass post-incident evaluations to continually refine and strengthen the organization’s overall security posture. Failure to adequately prepare and respond to data breaches can result in severe consequences, underscoring the necessity of a proactive and well-rounded approach to data breach response strategies.
Key Components of Data Breach Response Strategies
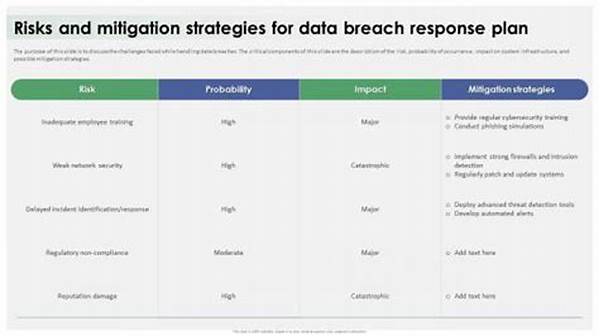
1. Detection and Identification: Implement systems and protocols that enable the early detection and identification of breaches.
2. Containment Measures: Define procedures to swiftly contain the breach and prevent further data loss or damage.
3. Communication Plan: Establish a clear communication plan for notifying affected parties and regulatory bodies.
4. Investigation and Analysis: Conduct detailed forensic analyses to understand the breach’s cause and impact.
5. Post-Incident Evaluation: Review and refine strategies post-incident to enhance future response efforts.
Building Effective Data Breach Response Strategies
Organizations must prioritize the formation of a dedicated response team, consisting of IT professionals, legal experts, and communication specialists, to oversee and manage breach incidents. Such teams are essential to ensure a coordinated and comprehensive response that addresses all facets of a breach, from technical containment to public relations. Furthermore, data breach response strategies should integrate periodic training and simulation exercises to keep the response team prepared and informed about the latest threats and response techniques.
In addition, data breach response strategies ought to include clear policy frameworks that define roles, responsibilities, and procedures throughout the organization. These frameworks ensure that every member of the organization is aware of their role in preventing, detecting, and responding to data breaches. By solidifying these internal structures, organizations can enhance their resilience to breaches and nurture a culture of proactive cybersecurity vigilance.
Detailed Overview of Data Breach Response Strategies
1. Early Detection Mechanisms: Implement systems to identify breaches at inception.
2. Isolation Techniques: Use network segmentation to contain breaches effectively.
3. Transparent Communication: Notify relevant stakeholders swiftly to manage expectations and legal commitments.
4. Comprehensive Investigations: Conduct thorough analyses to uncover all breach aspects.
5. Continuous Training: Regularly update team skills to stay abreast of evolving threats.
6. Regulatory Compliance: Align strategies with legal obligations to avoid penalties.
7. Crisis Management Coordination: Ensure all departments are prepared to work together during a breach.
8. Data Recovery Plans: Develop strategies for recovering and securing compromised data.
9. Update Security Infrastructure: Continually enhance systems based on breach learnings.
10. Employee Awareness: Cultivate an organizational culture focused on data security vigilance.
Challenges in Implementing Data Breach Response Strategies
Organizations frequently encounter difficulties when executing data breach response strategies, often due to limited resources or inadequate preparedness. One significant challenge is keeping pace with rapidly evolving cyber threats. Organizations must stay informed about emerging attack vectors and continuously update their response strategies accordingly. Another challenge lies in the effective communication and coordination between different departments, which is crucial for executing a swift and unified response.
Moreover, balancing immediate response actions with longer-term security measures presents another layer of complexity. While prompt containment and notification are vital, it is equally important to invest in systemic changes that prevent future occurrences. This balance requires organizations to not only focus on immediate incident management but also to conduct ongoing evaluations of their security practices, ensuring that the lessons learned from each breach are translated into stronger safeguards.
Future Prospective of Data Breach Response Strategies
As digital ecosystems expand and the sophistication of cyber threats escalates, the future of data breach response strategies will likely involve increased reliance on artificial intelligence and automation. These technologies can enhance detection capabilities and deliver swift responses, minimizing human error and response times. The integration of AI-driven security systems can analyze large volumes of data in real-time, identifying patterns that signify a potential breach more effectively than traditional methods.
Additionally, the collaborative efforts of industry-wide initiatives and governmental support will play a critical role in amplifying the effectiveness of data breach response strategies. By sharing insights and standardizing practices across sectors, organizations can collectively raise the bar for cybersecurity. As a result, the focus on data breach response strategies will shift towards a more unified global approach, combining innovation and shared expertise to combat the increasingly sophisticated landscape of cyber threats effectively.
Summary of Data Breach Response Strategies
In conclusion, data breach response strategies are vital instruments in the battle against cyber threats. These strategies encompass a multifaceted approach, emphasizing early detection, swift containment, comprehensive investigation, and transparent communication. Organizations must invest in building robust frameworks and dedicated teams to handle incidents effectively and mitigate potential damages. Moreover, continuous training and adherence to regulatory guidelines are pivotal in maintaining readiness against evolving threats.
The rapidly evolving nature of cyber threats necessitates adaptive and proactive data breach response strategies that integrate technological advancements such as AI and machine learning. Collaborative efforts across industries, coupled with governmental support, will bolster these strategies, enabling organizations to respond more effectively to breaches. By prioritizing a holistic approach and fostering an organizational culture centered on cybersecurity, enterprises can not only protect their digital assets but also reinforce stakeholder trust and safeguard their reputation in an increasingly interconnected world.