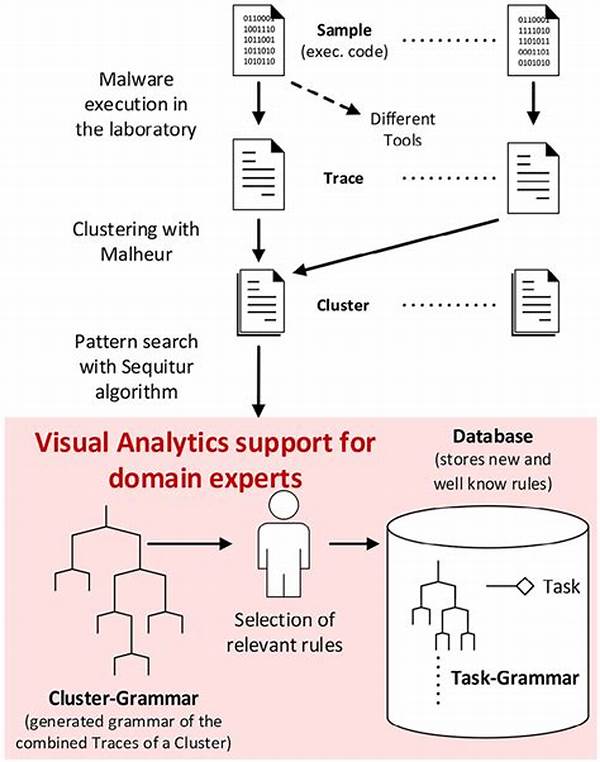
In today’s digital age, the threat posed by malicious software continues to grow exponentially. To mitigate these risks, security experts must employ sophisticated techniques to identify and analyze the behavioral patterns of malware. This process, known as malware behavior pattern identification, is vital to developing proactive strategies for defense against cyber threats.
Understanding Malware Behavior Patterns
Malware behavior pattern identification involves observing the activities and characteristics of malicious software to deduce its intentions and potential impacts on systems. These patterns are deciphered through meticulous monitoring and analyzing the malware’s lifecycle, which includes its propagation methods, execution patterns, and system modifications. Such understanding aids in anticipating future malware tactics, leading to the development of more robust security protocols. By examining these patterns, security professionals can distinguish between various malware families, enabling them to deploy more targeted and effective countermeasures. This comprehensive identification process is integral for bolstering digital security frameworks in organizations, enhancing their ability to withstand complex cyber threats.
Techniques in Malware Analysis
1. Static Analysis: Examination of malware code without execution to identify potential behavior patterns.
2. Dynamic Analysis: Running malware in a controlled environment to observe behavior pattern variations.
3. Behavioral Analysis: Monitoring malware’s interactions with the operating system in real-time for detailed pattern identification.
4. Heuristic Analysis: Utilization of algorithms to detect new malware through behavior pattern anomalies.
5. Machine Learning Models: Leveraging AI to recognize unprecedented malware behavior patterns.
Importance of Identifying Malware Patterns
Malware behavior pattern identification is critical in preemptive cybersecurity measures. By identifying these patterns, organizations can enhance their ability to predict and neutralize emerging threats before they manifest into significant breaches. This proactive stance reduces the impact of cyber incidents, safeguarding sensitive data and maintaining operational continuity. Organizations that consistently engage in identifying malware behaviors can build resilient infrastructures. This practice ensures that security measures are not just reactive but sufficiently proactive, thus deterring potential cybercriminal activities. Furthermore, a comprehensive understanding of malware behavior patterns enables informed decision-making in cybersecurity strategy formulation, leading to a more secure digital environment.
Real-world Applications
1. Enhanced Threat Intelligence: Malware behavior pattern identification provides richer datasets, helping in threat intelligence.
2. Improved Security Software: Developing security programs that preemptively block identified malicious patterns.
3. Incident Response Optimization: Empowering faster response tactics by recognizing signature patterns.
4. Policy Formulation: Shaping security policies based on identified malware behaviors.
5. Risk Assessment: Understanding malware patterns contributes to accurate risk evaluation.
6. Advanced Intrusion Detection Systems (IDS): Utilizing identified patterns to alert and mitigate threats in real-time.
7. Network Security Enhancements: Adopting behavior identification to secure network perimeters effectively.
8. Employee Training: Educating staff on recognizing behavior patterns to prevent malware execution.
9. Collaboration with Law Enforcement: Sharing pattern identification findings to aid in cybercrime investigations.
10. Periodic Security Audits: Incorporating malware behavior insights into regular security evaluations for continuous improvement.
Challenges in Pattern Identification
Malware behavior pattern identification, while advantageous, presents several challenges. Many sophisticated malware variants employ obfuscation techniques to disguise their operations, making it difficult for analysts to pinpoint definitive behavior patterns. Furthermore, the sheer volume of malware circulating the internet requires substantial resources for analysis, which can strain even robust cybersecurity teams. Moreover, the rapid evolution of malware means that behavior pattern databases must be continually updated to remain relevant. This dynamic environment necessitates a perpetual learning curve for cybersecurity personnel. Overall, despite these challenges, the skillful identification of malware patterns remains indispensable for fortifying cyber defenses.
Future Perspectives
As cyber threats advance, the methods of malware behavior pattern identification must evolve correspondingly. Emerging technologies, such as artificial intelligence and machine learning, are anticipated to play an instrumental role in refining these identification techniques. By integrating AI, security experts can automate and enhance the precision of pattern recognition, even predicting future malware trends before they materialize. Moreover, fostering a culture of continuous learning and adaptation will prove essential for cybersecurity professionals to keep pace with the ever-changing threat landscape. Collaborative efforts across the international security community will further strengthen the collective endeavor to combat malware, ensuring a safer cyber environment for all.
Summary of Malware Behavior Pattern Identification
In conclusion, malware behavior pattern identification is an indispensable component of modern cybersecurity practices. By discerning the distinctive characteristics and behaviors of malicious software, organizations can formulate preemptive defense strategies that significantly curtail the potential harm inflicted by cyber threats. This meticulous process not only enhances immediate tactical responses but also facilitates the development of long-term strategic frameworks geared towards cybersecurity resilience. As the complexity of cyber threats continues to escalate, the ability to accurately identify and interpret malware behavior patterns will become ever more critical for safeguarding digital assets. Integrating innovative technologies and nurturing international collaboration will undoubtedly amplify these efforts, fostering a more secure global digital landscape. Through comprehensive analysis and persistent vigilance, organizations can fortify their defenses against the ever-present tide of malware.