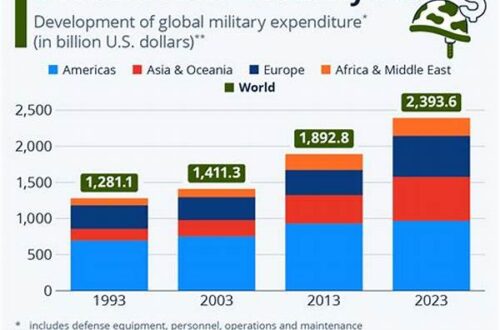
Introduction to Cybersecurity Arms Control Frameworks
In today’s interconnected world, the burgeoning threats of cyber warfare necessitate comprehensive strategies to ensure global security. As digital technologies evolve, their misuse becomes alarmingly prevalent, prompting international communities to consider cybersecurity arms control frameworks. These frameworks are designed to regulate the development, proliferation, and deployment of cyber capabilities that could potentially compromise national and global stability. Policymakers and security experts underscore the vital role of these frameworks in mitigating the risks associated with cyber conflicts.
The establishment of effective cybersecurity arms control frameworks is underscored by their potential to enhance global cooperation. By fostering dialogue among nations, these frameworks encourage the exchange of information about emerging cyber threats and promote the adoption of best practices in cybersecurity. Through international treaties and agreements, they aim to create a standardized set of norms and regulations that govern cyber activities. Such measures are imperative, as they not only contribute to the reduction of cyber-related threats but also build trust among nations.
Cybersecurity arms control frameworks, therefore, emerge as pivotal instruments in safeguarding digital infrastructure worldwide. They offer a structured approach to managing the complexities of cybersecurity within a global context, emphasizing the necessity for collaboration and mutual understanding between states. As cyber threats continue to evolve, the international community’s commitment to these frameworks becomes increasingly critical, manifesting the need for robust mechanisms that are adaptive to the dynamic nature of cyber threats.
Key Components of Cybersecurity Arms Control Frameworks
1. International Law and Norms: Cybersecurity arms control frameworks often incorporate international laws and norms to ensure states adhere to established standards. This legal basis promotes accountability, discouraging malicious cyber activities.
2. Cooperative Measures: Such frameworks encourage international cooperation, fostering trust and information-sharing among nations. This synergy helps address global cybersecurity challenges efficiently.
3. Verification Mechanisms: To ensure compliance, cybersecurity arms control frameworks integrate verification mechanisms, similar to traditional arms control treaties. These processes are vital for maintaining transparency.
4. Capacity Building: Frameworks often include provisions for capacity building, enabling nations, especially developing ones, to enhance their cybersecurity capabilities and resilience.
5. Crisis Management Protocols: Establishing crisis management protocols is crucial within these frameworks. They provide guidance on conflict resolution and mitigating escalation risks during cyber incidents.
Importance of International Collaboration
International collaboration plays a crucial role in the success of cybersecurity arms control frameworks. The global nature of cyber threats necessitates a coordinated response, as no single nation can tackle these challenges alone. By pooling resources and expertise, countries can devise comprehensive strategies to counteract cyber threats. Collaborative efforts, such as joint exercises and shared research initiatives, enable nations to stay ahead of adversaries who exploit cyber vulnerabilities for nefarious purposes.
Cybersecurity arms control frameworks benefit from international collaboration by fostering a culture of adherence to established norms. As countries work together, they can set benchmarks for responsible state behavior in cyberspace, deterring potential aggressors. Furthermore, by partaking in dialogue and negotiations, states can address concerns related to privacy, data protection, and human rights within the context of cybersecurity. This collective approach ensures that frameworks remain equitable and adaptable to the changing cyber landscape.
Challenges in Implementing Frameworks
Implementing cybersecurity arms control frameworks presents a myriad of challenges. One primary hurdle is the differing cybersecurity capabilities and priorities among nations. These disparities can create friction in reaching consensus on issues such as verification and enforcement. Furthermore, the rapid evolution of cyber threats necessitates constant updates to frameworks, demanding flexibility in negotiation and implementation processes.
Another challenge lies in the attribution of cyber incidents. Pinpointing perpetrators remains complex, often hindering the enforcement of accountability measures. Cybersecurity arms control frameworks must, therefore, incorporate advanced technological solutions to accurately attribute cyber attacks, ensuring that violators are appropriately sanctioned.
The Role of Technology in Cybersecurity Frameworks
Technology plays an instrumental role in the efficacy of cybersecurity arms control frameworks. Innovations in cybersecurity technology provide both opportunities and challenges in the implementation of these frameworks. On one hand, advanced tools and techniques enhance the capabilities of states to defend against cyber threats and streamline verification processes. However, they also necessitate ongoing investment in research and development to remain relevant.
Cybersecurity arms control frameworks must evolve in tandem with technological advancements to maintain their effectiveness. As cyber attack vectors grow more sophisticated, frameworks must integrate cutting-edge technologies that can detect and neutralize threats with precision. This continuous adaptation ensures that frameworks remain resilient and robust in an increasingly complex digital environment.
Future Prospects of Cybersecurity Arms Control Frameworks
Looking to the future, the development of comprehensive cybersecurity arms control frameworks remains a priority for the international community. As cyber threats continue to proliferate, there is a growing recognition of the need for enhanced global cooperation and tighter regulatory measures. The prospect of new treaties and agreements highlights the potential for establishing a more structured approach to international cybersecurity governance.
Furthermore, the integration of emerging technologies such as artificial intelligence and machine learning offers promising avenues for strengthening cybersecurity arms control frameworks. These technologies could provide new capabilities for threat detection, response, and prevention, further enhancing the resilience of digital infrastructure. Ultimately, the future of cybersecurity arms control frameworks hinges on the ability of nations to adapt and respond collectively to the evolving landscape of cyber warfare.
Summary of Cybersecurity Arms Control Frameworks
In conclusion, cybersecurity arms control frameworks represent a fundamental component in the safeguarding of global digital infrastructure. As cyber threats continue to pose significant risks to national security and international stability, these frameworks emphasize the importance of international collaboration and mutual understanding. By fostering dialogue and cooperation, they establish norms and regulations that govern state behavior in cyberspace, deterring potential aggressors.
Moreover, the successful implementation of cybersecurity arms control frameworks relies on the ability to overcome challenges such as differing national capabilities and the attribution of cyber incidents. Recognizing the instrumental role of technology, these frameworks must adapt to leverage emerging technological advancements. As the international community continues to prioritize cybersecurity, the frameworks designed to control and manage cyber arms become increasingly vital, highlighting the necessity for continued investment and innovation in protecting the global cyber ecosystem.