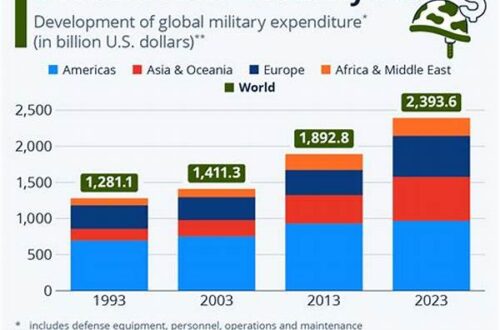
In today’s hyper-connected digital world, the seamless sharing of information is both inevitable and essential. However, the need to safeguard personal privacy while disseminating information has given rise to the development of various anonymous information sharing techniques. These techniques serve as vital tools in preserving the anonymity and confidentiality of users, allowing for the free exchange of data without compromising identities. This article delves into the mechanisms of these techniques and their implications for personal privacy and security.
The Importance of Anonymous Information Sharing Techniques
Anonymous information sharing techniques serve a critical role in protecting the identities of individuals who wish to share information without revealing their personal details. These techniques are particularly significant in environments where privacy concerns are paramount, such as in whistleblowing, reporting of sensitive incidents, or conducting secure communications. By maintaining anonymity, these methods encourage more open and honest exchanges of information, facilitating trust and collaboration across various domains. Furthermore, they help to shield users from potential negative consequences of sharing sensitive information, such as harassment or discrimination. The intricacies of these techniques not only empower individuals to maintain control over their personal data but also uphold the ethical standards of data sharing. As technology advances, the development and refinement of anonymous information sharing techniques continue to evolve, offering innovative solutions that address diverse privacy challenges. The adoption of these practices is essential for fostering an environment where information can flow freely and securely, without compromising the safety and anonymity of users.
Key Components of Anonymous Information Sharing Techniques
1. Encryption Technologies: Encryption serves as a fundamental aspect of anonymous information sharing techniques, ensuring that data remains confidential and inaccessible to unauthorized entities.
2. Decentralized Networks: These networks distribute data across multiple nodes, reducing the risk of centralized control and enhancing user anonymity.
3. Anonymous Browsing Tools: Tools such as Tor facilitate anonymous communication by obscuring the user’s identity and location.
4. Secure Communication Channels: End-to-end encryption ensures that messages are only accessible to the intended recipients, maintaining privacy.
5. Anonymous Feedback Platforms: These platforms allow individuals to share information or feedback without revealing their identity, thus promoting open communication.
Challenges and Solutions in Implementing Anonymous Information Sharing Techniques
While anonymous information sharing techniques provide considerable benefits, they also present certain challenges. One key challenge is the potential misuse of these techniques for illicit activities, which poses legal and ethical dilemmas. Balancing the protection of anonymity with the need to prevent illegal acts is a complex task. To address this, ongoing collaboration between technology developers and regulatory bodies is imperative to establish frameworks that ensure responsible use. Another challenge is the technical complexity involved in implementing these techniques, which requires significant expertise and resources. To overcome this, raising awareness about these techniques and investing in user-friendly technologies is crucial. Educating users on best practices for maintaining anonymity is equally important to ensure effective utilization. Tackling these challenges through a combination of policy-making, technological innovation, and public education will be crucial for the sustainable advancement of anonymous information sharing techniques in the ever-evolving digital landscape.
Ethical Considerations of Anonymous Information Sharing Techniques
The deployment of anonymous information sharing techniques necessitates a careful examination of ethical considerations. Privacy and security must be balanced with the responsibility to prevent harm. These techniques should be employed in a manner that respects the rights of all parties involved while preventing misuse. Establishing clear ethical guidelines is essential to uphold the integrity of information sharing practices. It is crucial to foster a culture of accountability, where transparency in the application of these techniques is prioritized. Organizations and individuals must be guided by principles that safeguard not only individual privacy but also communal security. By maintaining ethical standards, the deployment of these techniques can contribute positively to societal discourse, empowering individuals without enabling unethical conduct.
Future Prospects for Anonymous Information Sharing Techniques
As technology continues to evolve, the future of anonymous information sharing techniques looks promising. The integration of artificial intelligence and machine learning can potentially enhance these techniques, making them more adaptive and resilient. Innovations in blockchain technology also hint at new possibilities for secure and anonymous data exchanges. However, with these advancements come responsibilities; it is crucial to remain vigilant about emerging threats and to continuously fortify privacy measures. Research and development in this field should be encouraged and supported to spearhead breakthroughs that safeguard anonymity and facilitate secure information sharing. Collaborative efforts among technology developers, policymakers, and stakeholders are imperative to shape the future of information sharing that is both anonymous and ethical.
Policy Implications of Anonymous Information Sharing Techniques
The widespread adoption of anonymous information sharing techniques has significant implications for policy and regulation. Policymakers must strive to create a balanced regulatory framework that protects user anonymity while preventing misuse. Crafting effective legislation requires a nuanced understanding of the technologies and their societal impacts. International cooperation and dialogue will be essential in harmonizing regulations and establishing global standards. Such policies should promote innovation, protect individual rights, and deter malicious activities. By forming comprehensive policies, governments can ensure that the benefits of these techniques are maximized, contributing to enhanced privacy and security in the digital age.
Summary of Anonymous Information Sharing Techniques
In summary, anonymous information sharing techniques represent a crucial facet of today’s digital environment, supporting privacy and security while enabling the free flow of information. These techniques encompass a range of technologies and methodologies designed to obscure user identities and safeguard data. They play an essential role in various sectors, providing avenues for secure communication and information exchange. While challenges related to misuse and implementation persist, continuous innovation and robust regulatory frameworks can address these issues. Ethical considerations remain central to the deployment of these techniques, ensuring a balance between privacy and responsibility. Looking forward, the integration of emerging technologies promises to expand the capabilities and reach of these techniques, offering new solutions to privacy dilemmas. Ultimately, the successful adoption of anonymous information sharing techniques will depend on collective efforts to prioritize privacy, foster innovation, and uphold ethical standards in the digital realm. As society navigates the complexities of data sharing, these techniques will continue to serve as vital tools in protecting individual freedom and promoting a secure, trustworthy environment for information exchange.