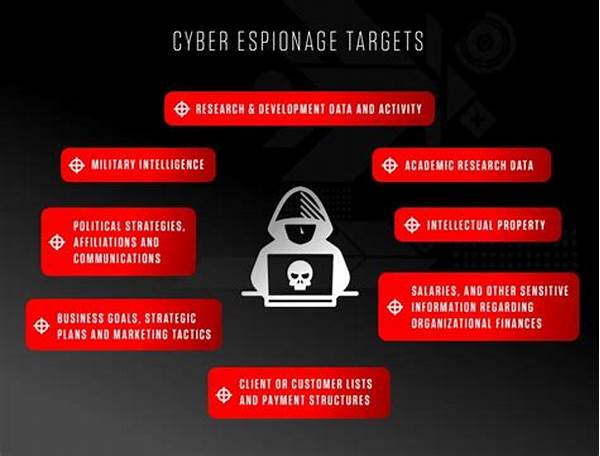
In an era characterized by rapid technological advancement and global interconnectedness, espionage has emerged as a significant threat to national security and corporate interests alike. As intelligence operations become more sophisticated, organizations and governments must engage in robust and proactive measures to mitigate these risks. The following discourse delineates the essential steps to neutralize espionage attempts, employing a methodical approach to safeguard sensitive information. This treatise aims to elucidate the requisite strategies aimed at preserving the integrity of confidential data amidst the ever-evolving landscape of espionage.
Understanding Espionage Dynamics
The foundational step in neutralizing espionage attempts involves an intricate understanding of the dynamics at play. This necessitates a thorough grasp of the methods employed by espionage agents, who may exploit both technological vulnerabilities and human weaknesses. Understanding these dynamics facilitates the development of targeted countermeasures designed to thwart infiltration. The essence of safeguarding information lies in recognizing and anticipating the myriad tactics utilized by adversaries. By adopting a vigilant stance, organizations can detect and forestall attempts to compromise their operations. Thus, a comprehensive understanding of espionage dynamics is incumbent upon any entity that seeks to implement effective steps to neutralize espionage attempts.
Organizations must invest in education and training endeavors tailored to increase awareness among staff members regarding potential espionage threats. This knowledge equips personnel with the intuition necessary to identify suspicious activities and report them promptly. Furthermore, fostering an informed workforce contributes to cultivating a security-oriented culture. Such a culture embodies resilience against espionage attempts and is pivotal in realizing the steps to neutralize espionage attempts. Consequentially, an organization’s fortification against espionage threats hinges on a well-informed and proactive workforce adept at identifying and mitigating potential risks.
Strategic Countermeasures
The deployment of strategic countermeasures is integral to the steps to neutralize espionage attempts, encompassing both technological implementations and human-centric strategies. Organizations should prioritize the adoption of state-of-the-art cybersecurity technologies to protect critical networks from unauthorized access. This includes utilizing encryption protocols, firewalls, and intrusion detection systems designed to identify and mitigate threats in real-time.
To augment these technological solutions, human-centric strategies must be integrated, such as establishing strict vetting procedures for personnel with access to sensitive information. Conducting comprehensive background checks and periodic evaluations aids in identifying potential vulnerabilities within the organization. In concert, these measures form a robust defense against infiltration and exfiltration attempts, enhancing the organization’s resilience to espionage activities.
Multi-Layered Surveillance Systems
Implementing a multi-layered surveillance system is another critical facet of the steps to neutralize espionage attempts. These systems offer a comprehensive approach to monitoring and protecting organizational assets. Integrating physical security measures with advanced digital surveillance tools ensures thorough coverage of potential threat vectors, effectively deterring espionage activities.
Moreover, leveraging artificial intelligence and machine learning technologies enhances the efficacy of surveillance systems by autonomously identifying suspicious patterns and anomalies. This proactive approach allows for swift action in addressing threats before they escalate, reinforcing the organization’s capacities to neutralize espionage attempts effectively.
Training and Awareness Programs
Education is paramount among the steps to neutralize espionage attempts, making training and awareness programs indispensable components of an organization’s defense strategy. Regular workshops and seminars should be conducted to update personnel on emerging threats and best practices in handling sensitive information. These programs cultivate a conscientious workforce adept at identifying and reporting potentially harmful activities.
Encouraging a security-first mindset within the organizational culture instills a sense of responsibility among employees, fostering collective vigilance against espionage attempts. By equipping personnel with the competencies necessary to recognize espionage threats, organizations fortify their defenses and enhance their ability to neutralize such threats effectively.
Collaboration with Intelligence Agencies
Strengthening collaboration with intelligence agencies constitutes a pivotal dimension of the steps to neutralize espionage attempts. Engaging with external experts and institutions provides valuable insights and resources that facilitate the development of targeted counter-espionage strategies. Sharing intelligence enhances situational awareness and augments an organization’s capacity to preemptively thwart espionage activities.
Such collaboration fosters an environment conducive to proactive threat identification and mitigation, employing a comprehensive approach to counterintelligence. Furthermore, this partnership allows for the exchange of best practices and experiences, significantly bolstering an organization’s resilience against espionage threats and reinforcing its strategic defenses.
Maintaining Operational Security
Maintaining stringent operational security is instrumental in the steps to neutralize espionage attempts. This encompasses the implementation of robust access controls, ensuring that only authorized personnel can gain entry to sensitive data and facilities. Enforcing strict protocols minimizes the risks associated with insider threats and data breaches, safeguarding the organization’s critical assets.
Periodic audits and evaluations of security policies and practices are essential to identify vulnerabilities and implement necessary enhancements. A proactive approach to operational security management fortifies an organization’s defenses, ensuring ongoing preparedness to confront and neutralize espionage attempts effectively.
Summary
In conclusion, the steps to neutralize espionage attempts necessitate a multifaceted strategy encompassing an understanding of espionage dynamics, the deployment of strategic countermeasures, and the implementation of advanced surveillance systems. It is imperative for organizations to invest in both technological solutions and human-centric strategies, ensuring a comprehensive approach to mitigating espionage threats.
A culture of security awareness and collaboration with intelligence agencies further enhances an organization’s resilience against espionage activities. By maintaining robust operational security and fostering a security-first mindset, organizations can effectively safeguard their assets and maintain the integrity of their operations amidst an evolving threat landscape. Through these steps to neutralize espionage attempts, entities can remain vigilant and resilient in the face of both current and future challenges.