In the realm of information security and digital infrastructure, user identity lifecycle management holds paramount significance. It is the systematic administration of a user’s identity within an organization’s technological ecosystem, encompassing their creation, maintenance, and eventual deletion from a directory service. This process ensures that appropriate access rights are granted, maintained, and revoked responsibly to secure critical data and infrastructures. Ensuring effective management of user identities is crucial in today’s digital age, where security breaches and unauthorized access can have devastating consequences. This comprehensive approach must be robust, agile, and adaptive to changing organizational needs and technological advancements.
Importance of User Identity Lifecycle Management
The implementation of user identity lifecycle management is crucial for maintaining a secure and efficient digital workspace. It starts with the initial onboarding of a user, granting them appropriate credentials and access rights tailored to their job responsibilities. As a user’s role within an organization evolves, their access needs may change, requiring timely updates to their identity credentials. This dynamic adjustment is critical in preventing unauthorized access and potential cyber threats. Regular reviews and audits of user identities ensure compliance with regulatory requirements and enhance overall security posture.
In the offboarding phase, user identity lifecycle management becomes imperative in swiftly removing access rights once a user exits the organization. This step prevents any lingering access that could be exploited maliciously. Automation plays a significant role in streamlining these processes, minimizing human errors, and enhancing operational efficiency. Organizations must adopt a strategic approach, integrating advanced tools and technologies to ensure all aspects of the identity lifecycle are managed effectively.
Key Components of User Identity Lifecycle Management
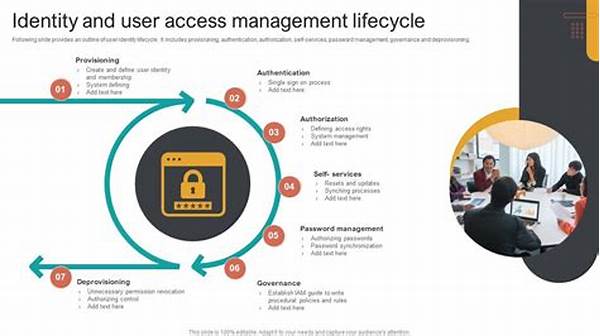
1. Onboarding Users: Central to user identity lifecycle management is the onboarding process, which involves the creation of a user’s digital identity and assigning them appropriate access based on their role within the organization.
2. Access Rights Management: Continuous evaluation and adjustment of user access rights are vital to ensure compliance and maintain security standards, which are integral to user identity lifecycle management.
3. Automation: Leveraging automation in user identity lifecycle management minimizes human error, speeds up processes, and ensures uniformity across the user management spectrum.
4. Auditing and Compliance: Regular audits are indispensable in ensuring that user access aligns with organizational policies, a core aspect of effective user identity lifecycle management.
5. Offboarding Users: A swift and efficient offboarding process is essential in user identity lifecycle management to prevent security breaches from former employees or stakeholders.
Challenges in User Identity Lifecycle Management
Managing user identities across diverse platforms presents several challenges. Every organization needs a tailored approach to user identity lifecycle management that aligns with its unique operational demands and regulatory frameworks. One primary challenge is maintaining consistency in user access controls across various systems, especially as new technologies and systems are integrated into the organizational ecosystem. Ensuring that these controls remain robust yet flexible enough to adapt to ongoing changes in user roles and responsibilities can be daunting.
Another considerable challenge in user identity lifecycle management includes the need for continuous monitoring and compliance with ever-evolving legal and regulatory requirements concerning data protection and privacy. With the increasing frequency of cyber threats, the necessity for a resilient security infrastructure that safeguards user identities becomes imperative. Organizations must also address internal challenges such as resource allocation, training, and investment in appropriate technology to facilitate effective identity management.
Best Practices for User Identity Lifecycle Management
Implementing best practices in user identity lifecycle management is essential for ensuring security and operational efficiency. One effective practice is adopting a strong authentication mechanism, such as multi-factor authentication (MFA), which enhances security by requiring multiple verification methods. Ensuring timely review and update of access rights, especially as user roles change, is crucial for minimizing the risk of unauthorized access.
Routine auditing of user identities to verify compliance with internal policies and external regulations is an indispensable best practice. Also, employing the principle of least privilege, which involves granting users the minimum levels of access—or permissions—needed to perform their job functions, is a fundamental aspect of secure user identity lifecycle management. Automation tools can further streamline administrative tasks, reducing the potential for human error and enhancing accuracy. Training employees about security policies and best practices is equally important in fostering a culture of cybersecurity awareness.
Strategic Framework for Effective User Identity Lifecycle Management
A comprehensive strategy for user identity lifecycle management integrates technology, processes, and people to safeguard digital assets effectively. Organizations should leverage identity management solutions that offer scalability and interoperability with existing systems to facilitate seamless identity integration across platforms. This strategic framework should be underpinned by well-defined policies and operational guidelines tailored to meet specific organizational needs.
Collaboration between IT departments, information security teams, and organizational stakeholders is crucial in developing and maintaining a robust user identity lifecycle management system. Regular training and awareness programs help fortify an organization’s resilience against identity-related cyber threats. Furthermore, strategic investments in advanced technologies, such as artificial intelligence and machine learning, can enhance real-time threat detection and response capabilities, thus bolstering the organization’s security framework.
Conclusion
In summation, user identity lifecycle management is an essential component of modern IT infrastructures that necessitates a thoughtful approach combining technology and policy. As digital ecosystems continue to expand and evolve, the importance of managing user identities securely and efficiently cannot be overstated. Organizations must remain vigilant and proactive in adapting their identity management strategies to confront the continuous emergence of sophisticated cyber threats effectively.
By investing in comprehensive tools, enforcing stringent security protocols, and fostering a culture of awareness and accountability, businesses can ensure the integrity of their digital environments. Effective user identity lifecycle management not only protects sensitive data but also reinforces trust with customers and compliance with regulatory standards, thereby driving organizational success and resilience in the digital age.