In recent years, the landscape of cybersecurity has evolved dramatically, compelling organizations to reassess their protective measures. Cybersecurity threat management strategies have emerged as paramount to safeguarding digital assets, thereby ensuring the integrity, confidentiality, and availability of information. This imperative necessitates a comprehensive understanding of the digital environment, potential vulnerabilities, and proactive threat mitigation techniques. As cyber threats become increasingly sophisticated, organizations must adopt more robust and comprehensive measures to protect their digital infrastructure.
The Importance of Cybersecurity Threat Management Strategies
The significance of cybersecurity threat management strategies cannot be overstated in today’s digital age. These strategies play a crucial role in identifying, assessing, and mitigating risks associated with cyber threats. Organizations, whether big or small, rely heavily on digital infrastructure to store and process data. Consequently, they become potential targets for cybercriminals seeking unauthorized access to sensitive information. Implementing effective cybersecurity threat management strategies becomes essential to ensure the security of data and to protect against unauthorized breaches.
The first step in establishing effective cybersecurity threat management strategies is assessing the organization’s current cybersecurity posture. This assessment involves identifying potential vulnerabilities and weaknesses within the system that could be exploited by cyber threats. Once identified, these vulnerabilities must be prioritized based on their severity and the likelihood of exploitation. Organizations can then develop and implement tailored strategies to address these vulnerabilities, thus enhancing their overall cybersecurity framework.
Furthermore, regular monitoring and reviewing of cybersecurity policies are integral components of cybersecurity threat management strategies. This ongoing process ensures that strategies remain effective against evolving threats. By continuously updating security protocols and conducting regular security audits, organizations can cultivate a resilient defense mechanism against cyber threats. Ultimately, the implementation of comprehensive cybersecurity threat management strategies is vital not only for protecting sensitive data but also for maintaining trust and confidence among stakeholders and clients.
Components of Cybersecurity Threat Management Strategies
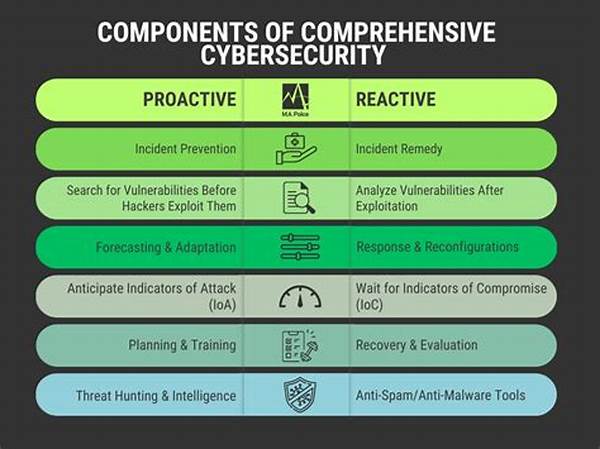
Effective cybersecurity threat management strategies encompass several key components. Risk Assessment involves evaluating potential threats and vulnerabilities to an organization’s digital assets. By understanding these risks, companies can prioritize their resources for optimal protection against cyber threats.
Incident Response Planning is a crucial aspect of cybersecurity threat management strategies. It ensures that organizations are prepared to handle and mitigate the impact of a cyber incident efficiently, thus minimizing potential damage and recovery time.Continuous Monitoring is essential for maintaining robust cybersecurity threat management strategies. This component involves the regular tracking of network activity to detect anomalies or unauthorized access, enabling prompt responses to potential threats.Employee Training and Awareness are pivotal in executing effective cybersecurity threat management strategies. By educating staff about potential threats and best practices, organizations can reduce human errors that often lead to security breaches.
Finally, Technology Integration is a cornerstone of cybersecurity threat management strategies. Implementing advanced security technologies, such as firewalls and encryption, fortifies an organization’s defenses against cyber adversaries.
Developing Comprehensive Cybersecurity Threat Management Strategies
To develop comprehensive cybersecurity threat management strategies, organizations must initiate an in-depth risk analysis to identify potential weaknesses within their digital infrastructure. Understanding specific threats pertinent to the organization is crucial in formulating targeted strategies. By leveraging threat intelligence, businesses can gain insights into emerging threats, thereby proactively adjusting their security measures. Furthermore, the development of a robust incident response plan is essential, ensuring swift action in the event of a security breach.
Another critical aspect of developing cybersecurity threat management strategies is stakeholder involvement. Engaging various departments and stakeholders within the organization fosters a culture of shared responsibility for cybersecurity. When everyone is aware of their roles in risk management, the organization’s defenses become collectively stronger. Regularly updating and testing cybersecurity protocols is also imperative to address evolving threats and to ensure the continued effectiveness of the strategies.
Implementing and Maintaining Cybersecurity Threat Management Strategies
Successfully implementing and maintaining cybersecurity threat management strategies require a systematic approach. Organizations should begin by deploying the necessary technical measures, such as firewalls, intrusion detection systems, and data encryption. These technologies act as the first line of defense against cyber threats. Integrating these tools with the organizational framework helps in mitigating risks comprehensively. Furthermore, establishing clear communication channels ensures that all employees are informed about updates in cybersecurity protocols.
Regular maintenance and updates are crucial for the ongoing effectiveness of cybersecurity threat management strategies. This involves conducting periodic assessments to identify new vulnerabilities and potential threats. By staying informed about the latest advancements and trends in cybersecurity, organizations can refine their strategies accordingly. Additionally, engaging third-party experts for independent audits can provide valuable external perspectives on an organization’s cybersecurity framework, leading to more robust threat management strategies.
The Role of Technology in Cybersecurity Threat Management Strategies
Technology plays a pivotal role in shaping effective cybersecurity threat management strategies. Advanced technologies such as artificial intelligence and machine learning have revolutionized threat detection and response mechanisms. These technologies analyze vast amounts of data to identify patterns and detect anomalies with precision. By automating threat detection and response, organizations can swiftly mitigate cyber threats before they escalate into significant breaches.
Moreover, cloud-based security solutions have become integral components of cybersecurity threat management strategies. These solutions provide scalability and flexibility, allowing organizations to adjust their security measures according to changing needs. They also offer real-time monitoring and threat intelligence, keeping organizations informed about the latest cyber threats. Ultimately, the integration of cutting-edge technologies enhances the overall efficacy of cybersecurity threat management strategies.
Enhancing Cybersecurity Threat Management Strategies through Collaboration
Collaboration is crucial in enhancing cybersecurity threat management strategies. Organizations should seek to establish partnerships with industry peers, government agencies, and cybersecurity experts, facilitating the exchange of threat intelligence and best practices. By participating in information-sharing forums, organizations can stay informed about the latest cyber threats and develop more robust threat management strategies.
Furthermore, collaboration within the organization itself is essential. Encouraging communication and cooperation between departments ensures that cybersecurity measures are comprehensively integrated into all aspects of the organization’s operations. Creating cross-functional teams that include IT, legal, and human resources representatives can lead to a more holistic approach in developing and implementing cybersecurity threat management strategies.
Conclusion: The Future of Cybersecurity Threat Management Strategies
In conclusion, as cyber threats continue to evolve, organizations must prioritize the development and implementation of robust cybersecurity threat management strategies. These strategies serve as the cornerstone for protecting digital assets and safeguarding sensitive information. By systematically identifying vulnerabilities, implementing proactive measures, and staying informed about emerging threats, organizations can mitigate risks effectively.
Moving forward, the future of cybersecurity threat management strategies will increasingly depend on technological advancements and cross-industry collaboration. Embracing innovations such as artificial intelligence, machine learning, and cloud-based solutions will be pivotal in enhancing threat detection and response capabilities. Furthermore, fostering partnerships and information sharing among various stakeholders will be key to staying ahead of cyber adversaries. By adopting a proactive and collaborative approach, organizations can fortify their defenses and confidently navigate the complexities of the digital landscape.