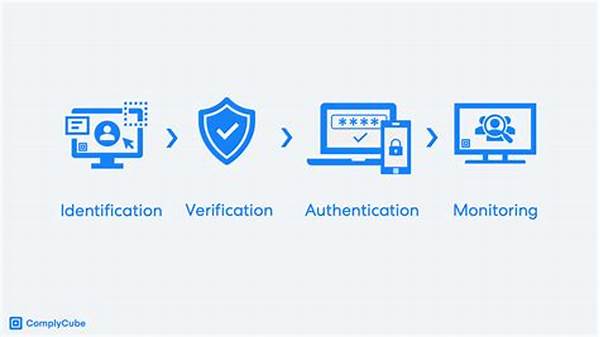
In today’s digital age, protecting personal information has become paramount, and the user identity verification process plays a crucial role in ensuring data security and privacy. This process involves various steps and techniques designed to authenticate an individual’s identity accurately. It is a fundamental practice not only for online platforms but also for institutions around the world seeking to safeguard their users and their data. This article delves into the intricacies of the user identity verification process, outlining its importance and the methodologies it employs to ensure robust security practices.
Importance of User Identity Verification Process
The user identity verification process is critical in enhancing the security infrastructure of digital platforms. This process is designed to confirm that an individual is who they claim to be, thereby preventing unauthorized access and potential data breaches. Through various measures such as biometric authentication, document verification, and two-factor authentication, the process adds multiple layers of security. The necessity of a robust user identity verification process has intensified with the increase in online transactions and interactions. By effectively verifying users, organizations can instill trust among users, which in turn fosters user engagement and satisfaction. This process is not merely a technical necessity but also a fundamental aspect of establishing credibility and legality in digital environments.
Furthermore, the user identity verification process serves as a deterrent to fraudulent activities. It ensures that the actual identity of users is verified before allowing access to sensitive applications or transactions. The protocols involved in identity verification are evolving, incorporating advanced technologies like artificial intelligence and machine learning to enhance accuracy and efficiency. These technologies enable quicker processing and identification, thus mitigating the risk of human error. Consequently, the user identity verification process acts as a foundational element in maintaining the integrity of digital platforms, providing a secure environment where users can interact without the fear of identity theft or fraud.
Moreover, regulatory compliance is another significant aspect addressed by the user identity verification process. Many jurisdictions mandate stringent verification processes to align with data protection regulations such as GDPR and CCPA. Ensuring compliance not only safeguards organizations from legal consequences but also strengthens consumer trust. As online interactions continue to grow, the user identity verification process remains a vital component in upholding the principles of data protection and user privacy, reinforcing the responsibility of organizations to protect individual identities diligently.
Components of User Identity Verification Process
1. Document Verification: The process begins with verifying government-issued identification documents. This aspect of the user identity verification process involves the scrutiny of features such as holograms and watermarks to confirm authenticity.
2. Biometric Authentication: Employing facial recognition or fingerprint scanning, biometric authentication adds an additional security layer to the user identity verification process by using unique personal attributes.
3. Two-Factor Authentication: A common practice in the user identity verification process is two-factor authentication, requiring users to provide two separate pieces of evidence to verify identity.
4. Knowledge-Based Verification: This component involves questioning users about personal information known only to them, thus adding another element of security in the user identity verification process.
5. Real-Time Verification: Leveraging modern technology, real-time verification ensures that the user identity verification process is both efficient and swift, minimizing delays while maintaining high accuracy.
Challenges in User Identity Verification Process
Despite its essential role, the user identity verification process is fraught with challenges that impact its efficacy. One of the primary challenges is balancing user experience with security demands. Overly stringent verification measures may deter users due to their complexity and time-consuming nature. Hence, organizations must design verification processes that are both comprehensive and user-friendly. Additionally, technological limitations in some regions hinder the implementation of advanced verification techniques, which can lead to vulnerabilities in the system. There is also the challenge of accommodating diverse user groups, necessitating adaptive verification methods that cater to various demographics and accessibility needs.
Another significant challenge is the continuous evolution of cyber threats. As hackers become more sophisticated, the user identity verification process must also evolve to anticipate and counter these threats. This requires constant updates and improvements to verification protocols. Moreover, privacy concerns arise when organizations collect and store sensitive personal data during the verification process, necessitating strict adherence to data protection laws and ethical data management practices. Developing a reliable user identity verification process, therefore, requires ongoing investment in technology and personnel training to address these dynamic challenges effectively.
Technological Innovations in User Identity Verification Process
Recent technological advancements have significantly influenced the user identity verification process. Artificial intelligence (AI) and machine learning are at the forefront, providing enhanced capabilities for identifying patterns and anomalies that may indicate fraudulent activity. AI-powered systems can efficiently process large volumes of data, reducing the time required for verification while minimizing human error. Machine learning algorithms continuously improve their accuracy and efficiency, adapting to new threats and vulnerabilities. Additionally, blockchain technology offers promising solutions by providing a decentralized and tamper-proof verification mechanism, further bolstering the security of the user identity verification process.
Biometric technologies have also seen substantial enhancements, offering secure and user-convenient methods for identity verification. Innovations such as voice recognition and iris scanning are becoming increasingly integrated into the user identity verification process. These technologies ensure a high level of security by capitalizing on unique biological traits. The integration of these technological innovations facilitates a more seamless verification process, accommodating the growing demand for secure and efficient identity verification in digital contexts.
Importance of Compliance in User Identity Verification Process
Compliance with regulatory standards is a non-negotiable aspect of the user identity verification process. Organizations are required to adhere to legislation and frameworks that dictate the protocols for data protection and verification practices. Anti-money laundering (AML) regulations and Know Your Customer (KYC) policies are just a few examples of directives that demand stringent identity verification measures. By complying with these regulations, organizations can mitigate risks associated with financial crimes and safeguard their reputation. Moreover, compliance ensures that the user identity verification process respects users’ privacy rights, preventing misuse of personal information while complying with legal obligations.
Non-compliance poses significant risks, including hefty fines and legal repercussions. Furthermore, failure to comply undermines consumer trust, which can adversely affect a company’s market position. Hence, establishing a compliant user identity verification process is imperative for any organization operating in the digital space. It demonstrates a commitment to ethical practices and adherence to global standards, building consumer confidence and fostering long-term loyalty.
Future Directions of User Identity Verification Process
Looking ahead, the user identity verification process is set to become even more integral to digital interactions. Advances in technology will continue to shape the methodologies used, making them more secure and seamless. However, with these advancements, the importance of user-friendly interfaces cannot be discounted. Organizations must focus on designing verification processes that offer high security without compromising on accessibility. Additionally, cross-industry collaborations could pave the way for standardized verification protocols, promoting interoperability and broader acceptance across digital platforms. As emerging technologies like quantum computing and advanced cryptography are explored, the potential for enhancing the user identity verification process is immense, promising a future of more secure and efficient digital ecosystems.
Furthermore, the integration of smart contract technologies could revolutionize how identity verification is conducted. Smart contracts can automate and enforce compliance with verification protocols, streamlining the process while ensuring adherence to established standards. As the digital landscape continues to evolve, the user identity verification process will undoubtedly remain a cornerstone of digital security, requiring continuous innovation and vigilance to meet the demands of an increasingly interconnected world.
Conclusion on User Identity Verification Process
In conclusion, the user identity verification process is an indispensable component of modern digital security frameworks. It provides a robust mechanism for safeguarding personal information and enhancing the trustworthiness of digital platforms. With a comprehensive verification process, organizations can effectively mitigate the risks of identity fraud and cybercrime, thus fostering a safe online environment for users. As technology continues to advance, so too must the methods and protocols associated with the user identity verification process, ensuring they remain relevant and resilient against new threats.
Ultimately, the user identity verification process is a dynamic and evolving practice, requiring constant adaptation and innovation to keep pace with the ever-changing landscape of digital threats. Through meticulous design, implementation, and compliance with regulatory standards, organizations can ensure a secure and efficient verification system. The future of identity verification will undoubtedly witness transformative advancements, paving the way for heightened security and user confidence in digital identities. As such, the user identity verification process remains a critical endeavor for organizations seeking to uphold security, compliance, and trust in the digital realm.