In the modern era of digital information and cyber interactions, safeguarding data is paramount. Access control and data integrity are two fundamental components essential for securing information stored in databases, transmitted over networks, and processed by applications. Access control ensures that only authorized users can access specific resources, while data integrity assures that information remains accurate and uncorrupted. Together, these concepts form the backbone of robust data security strategies.
The Core Principles of Access Control and Data Integrity
Access control is a critical mechanism that governs who or what can view or use resources in a computing environment. It involves the identification, authentication, and authorization processes to ensure that users have the necessary credentials to access specific data. Data integrity, on the other hand, focuses on maintaining the consistency, accuracy, and reliability of data throughout its lifecycle. It involves measures to prevent unauthorized data modification and mechanisms to detect and correct errors. Access control and data integrity are intertwined, as unauthorized access can lead to data breaches and compromise integrity. Robust systems must integrate these elements through encryption, access permissions, and auditing to ensure that the data remains secure and reliable at all stages of processing and storage.
Understanding the Mechanisms of Access Control and Data Integrity
1. Access control and data integrity are pivotal in establishing secure computing environments by preventing unauthorized data access and maintaining information accuracy.
2. Implementing effective access control and data integrity systems requires continuous monitoring to detect and respond to potential security threats swiftly.
3. Technologies like cryptographic techniques and multi-factor authentication significantly bolster access control and data integrity, enhancing overall security.
4. Access control systems often leverage role-based or attribute-based models to provide dynamic and context-sensitive data access rules.
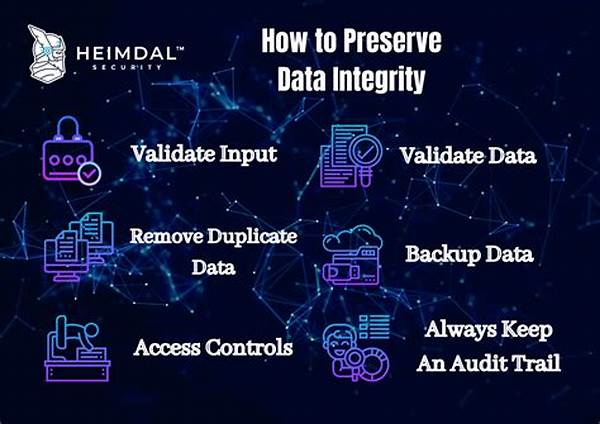
5. Maintaining data integrity involves regular data validation and verification processes to ensure information remains unaltered during storage or transmission.
Implementing Strategies for Access Control and Data Integrity
Establishing reliable access control measures is essential for organizations to protect sensitive information. One strategy involves using a comprehensive access control framework that includes authentication protocols like biometrics, passwords, or tokens to verify user identity. Subsequently, authorization determines the resources an authenticated user can access. This is often managed through role-based access control (RBAC), where permissions are assigned based on the user’s role within an organization. Additionally, audit logs are essential to track access activities and identify any unauthorized attempts. Regarding data integrity, using checksums and hash functions can detect errors or alterations in data during transfer. Consistent backup protocols are also crucial, providing data redundancy in case of corruption or loss. Both access control and data integrity require regular audits and updates to evolve with emerging threats and ensure compliance with security policies and standards.
Techniques to Enhance Access Control and Data Integrity
Improving access control and data integrity involves employing advanced techniques and tools that adapt to security challenges. One approach is incorporating contextual and behavioral analytics into access control systems to predict and mitigate unauthorized access attempts based on user behavior patterns. Another technique includes using advanced encryption methods to safeguard data at rest and during transit, thereby preserving data integrity. Implementing zero-trust architectures ensures that every access request thoroughly verifies before granting entry, thereby bolstering both access control and integrity. Furthermore, integrating machine learning algorithms helps in the anomaly detection process, identifying discrepancies in data that might indicate integrity issues. Regularly updating software and systems allows organizations to patch vulnerabilities that could be exploited to breach access controls or compromise data. Finally, user education and awareness programs play an integral role in maintaining high levels of data security and integrity by ensuring that all users adhere to best practices and company policies regarding data handling and access.
Policies for Access Control and Data Integrity
Establishing clear policies for access control and data integrity is vital for maintaining secure information assets. These policies typically outline the framework for granting access rights, detailing how users are authenticated and authorized to handle specific datasets. They define the roles and responsibilities of individuals in maintaining data security, ensuring everyone understands their part in protecting organizational data. Policies for data integrity highlight the procedures for data validation and error-checking processes, ensuring that all data entering or leaving the system maintains its original quality and accuracy. These might also specify the types of data correction methods employed when discrepancies are identified. Compliance with regulations such as GDPR or HIPAA often dictates specific access control and data integrity requirements, guiding organizations in crafting policies that adhere to legal standards.
Auditing and Compliance in Access Control and Data Integrity
With evolving threats in the digital landscape, auditing and compliance play crucial roles in access control and data integrity frameworks. Regular audits help identify weaknesses in existing systems, offering insights into areas requiring strengthening. Compliance ensures that data security measures align with industry standards and regulations, protecting organizations from legal repercussions associated with data breaches or corruption. Access logs and data transaction records serve as vital tools for audits, providing detailed accounts of user activities and data changes. An effective compliance strategy involves continuous monitoring and assessment, adjusting policies and procedures such that they meet or exceed regulatory expectations in terms of access control and data integrity measures.
Enhancing User Awareness for Better Access Control and Data Integrity
Educating users on best practices and potential risks is essential for effective access control and data integrity. Training programs should highlight the importance of secure passwords, recognizing phishing attempts, and following prescribed protocols for accessing and sharing data. Users equipped with this knowledge can better defend against security breaches, aiding in maintaining the integrity and confidentiality of data. The human element in cybersecurity cannot be overlooked, as unintentional errors often catalyze security incidents. An informed workforce, therefore, directly contributes to the robustness of access control systems and the reliability of data integrity, underpinning the overall security architecture of an organization.