In the contemporary theater of international relations and national security, espionage poses an enduring threat. The stakes involved are profoundly significant, impacting nations’ political dynamics, economic stability, and military potency. Consequently, advanced counter-espionage techniques implementation has become critical for governments, organizations, and security agencies worldwide. The adoption of these sophisticated strategies ensures both the detection and deterrence of espionage endeavors, fortifying national security apparatuses.
Importance of Advanced Counter-Espionage Techniques Implementation
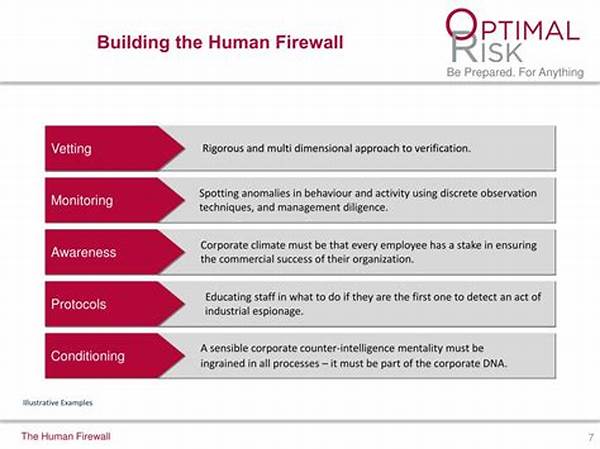
Advanced counter-espionage techniques implementation is paramount in safeguarding sensitive information against adversarial threats. These techniques are designed to anticipate espionage tactics, encompassing innovative surveillance methods and leveraging cutting-edge technology. By integrating these strategies, organizations can preemptively address potential breaches and mitigate the risks posed by espionage. This implementation requires a multifaceted approach, combining traditional espionage countermeasures with modern digital strategies. Furthermore, regular training and awareness programs are fundamental elements, ensuring security personnel remain adept in real-time threat detection and response.
Key Components of Advanced Counter-Espionage Techniques Implementation
1. Surveillance Technology: The cornerstone of advanced counter-espionage techniques implementation is the employment of cutting-edge surveillance technology to monitor and analyze potential threats in real-time.
2. Threat Intelligence: Advanced counter-espionage techniques implementation relies heavily on the aggregation and analysis of threat intelligence to stay ahead of evolving espionage tactics.
3. Cyber Defense: Strengthening cyber defenses is a critical aspect of advanced counter-espionage techniques implementation, protecting against digital intrusions and data breaches.
4. Human Intelligence: Despite technological advancements, human intelligence remains integral to advanced counter-espionage techniques implementation, offering valuable insights and intuition.
5. Interagency Collaboration: Effective advanced counter-espionage techniques implementation necessitates collaboration across agencies to pool resources and intelligence for enhanced protection.
Challenges in Advanced Counter-Espionage Techniques Implementation
The execution of advanced counter-espionage techniques implementation is fraught with complexities. One of the primary challenges lies in balancing the need for security with the preservation of civil liberties. The integration of robust surveillance systems can often raise privacy concerns, necessitating a judicious approach. Additionally, the rapid evolution of technological tools and techniques by adversaries requires continuous innovation and investment in counter-espionage strategies. Organizations must remain agile, embracing adaptive methodologies to effectively tackle emerging threats. Moreover, fostering a culture of security awareness within an organization is crucial, necessitating ongoing education and training initiatives to keep pace with espionage trends.
Best Practices in Advanced Counter-Espionage Techniques Implementation
1. Risk Assessment: Conduct regular risk assessments to identify vulnerabilities and inform the advanced counter-espionage techniques implementation process.
2. Technology Integration: Ensure seamless integration of cutting-edge technologies within existing systems for effective real-time threat detection.
3. Training Programs: Implement comprehensive training programs to enhance the skills and vigilance of personnel involved in counter-espionage activities.
4. Incident Response Plans: Develop robust incident response plans as part of advanced counter-espionage techniques implementation to address and mitigate breaches swiftly.
5. Data Protection Policies: Establish stringent data protection policies to safeguard sensitive information and minimize the risk of espionage.
6. Cultural Mindfulness: Promote a culture of mindfulness towards security within the organization, encouraging proactive rather than reactive measures.
7. External Collaboration: Engage with external experts and agencies for a broader perspective on threats and comprehensive counter-espionage strategies.
8. Continuous Monitoring: Maintain continuous monitoring systems to detect anomalies and identify potential espionage activities promptly.
9. Legal Compliance: Adhere to legal frameworks and regulations during advanced counter-espionage techniques implementation to avoid legal repercussions.
10. Resource Allocation: Allocate adequate resources to ensure effective deployment and maintenance of advanced counter-espionage measures.
Technological Advancements in Advanced Counter-Espionage Techniques Implementation
Technological advancements continue to shape the landscape of advanced counter-espionage techniques implementation. Innovations in artificial intelligence and machine learning have enhanced the capacity for threat identification and analysis, providing invaluable support in the early detection of espionage activities. These technologies, when integrated effectively, can augment traditional human intelligence methods, affording a more comprehensive approach to security. Additionally, advancements in encryption technologies have bolstered data protection, fortifying systems against unauthorized access. Nonetheless, with these advancements, organizations must remain vigilant against the dual-use nature of technology, where tools designed for security can also be exploited for subversion by adversaries.
Conclusion on Advanced Counter-Espionage Techniques Implementation
In conclusion, the implementation of advanced counter-espionage techniques is an indispensable facet of modern security protocols. By employing a comprehensive strategy that harmonizes technology with human expertise, organizations can substantially bolster their defense mechanisms against espionage threats. The ever-evolving nature of espionage tactics necessitates continuous innovation and adaptation in countermeasures, urging organizations to stay abreast of the latest developments in both technology and intelligence. Ultimately, the advanced counter-espionage techniques implementation is pivotal in preserving national security, organizational integrity, and the protection of sensitive information in an increasingly interconnected world.