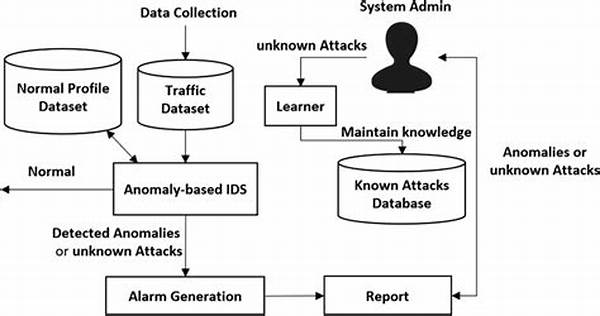
In the ever-evolving landscape of cybersecurity, anomaly-based intrusion detection systems (IDS) have become a pivotal component in safeguarding digital infrastructures. These systems are specifically designed to detect unusual patterns in network or system behavior, which may signify potential security threats. By employing advanced algorithms and machine learning techniques, anomaly-based intrusion detection systems can identify deviations from normal operating conditions and alert administrators to possible intrusions. Such systems are essential in identifying new, previously unknown threats that signature-based systems might miss, thus offering a sophisticated layer of defense against cyber threats.
The Mechanism of Anomaly-Based Intrusion Detection
Anomaly-based intrusion detection works on the principle of establishing a baseline of normal behavior through continuous monitoring and analysis of network traffic or system activities. When an activity diverges significantly from this established norm, it is flagged as potentially malicious. The ability of anomaly-based intrusion detection to learn and adapt to evolving network behaviors makes it particularly suited for environments with dynamic operational conditions. Additionally, its reliance on statistical measures and pattern recognition techniques allows it to operate efficiently across a range of network architectures and applications.
Benefits of Anomaly-Based Intrusion Detection
1. Adaptability: Anomaly-based intrusion detection systems are adaptable, continuously learning from network traffic to understand what constitutes “normal” behavior.
2. Advanced Threat Detection: These systems can identify previously unknown threats, unlike signature-based systems that only recognize known threats.
3. Scalability: Such systems can be scaled across various network sizes, ensuring they remain effective even as network infrastructure expands.
4. Real-time Monitoring: Anomaly-based intrusion detection provides real-time alerts to administrators, enabling swift response actions.
5. Reduced False Positives: Through advanced algorithms, these systems can minimize false positives, focusing on genuine threats.
Implementation Challenges in Anomaly-Based Intrusion Detection
Implementing an anomaly-based intrusion detection system poses several challenges. Firstly, the system requires substantial initial training to accurately establish a baseline of normal traffic or behavior. Moreover, tuning the system to reduce false positives without inadvertently missing actual threats is complex. Additionally, anomaly-based intrusion detection systems may demand considerable computational resources, which can be a constraint in resource-limited environments. Despite these challenges, careful planning and configuration can mitigate potential setbacks, allowing these systems to effectively protect against sophisticated cyber threats.
Key Considerations in Anomaly-Based Intrusion Detection
1. Training Data: Quality and quantity of data are crucial for accurate system training.
2. Baseline Accuracy: Establishing an accurate normal behavior baseline is fundamental.
3. Algorithm Selection: Choosing appropriate algorithms is vital for effective threat detection.
4. Resource Allocation: Ensuring sufficient computational resources to handle complex analyses is necessary.
5. Continuous Monitoring: Regular updates and adjustments are essential to maintain system efficacy.
6. Integration with Existing Systems: Compatibility with current infrastructure must be assessed.
7. Incident Response: Clear response protocols need to be established for action upon detection.
8. Cost-Benefit Analysis: Analysis to ensure the security benefits justify potential costs should be conducted.
9. Regulatory Compliance: Systems must adhere to relevant data protection regulations.
10. Security Personnel Training: Continuous training of staff is vital to effectively handle system alerts.
Advantages and Disadvantages of Anomaly-Based Intrusion Detection
Anomaly-based intrusion detection offers several advantages, including the ability to detect novel attacks and adaptability to changing environments. Its advanced learning algorithms can handle varied network conditions, making it suitable for complex systems. However, it also presents disadvantages, such as the potential for high false positive rates if not properly configured, and the demand for substantial computational resources. Organizations must weigh these pros and cons to determine the suitability of anomaly-based intrusion detection systems for their security needs.
The Future of Anomaly-Based Intrusion Detection
As cyber threats become increasingly sophisticated, the role of anomaly-based intrusion detection in cybersecurity is expected to grow. Future advancements may focus on enhancing detection accuracy and reducing resource consumption. Integrating artificial intelligence and machine learning further into these systems could provide more nuanced threat detection capabilities and predictive analysis, anticipating potential threats before they manifest. Consequently, ongoing research and development efforts in anomaly-based intrusion detection are crucial to maintaining robust cybersecurity defenses in the digital age.
Conclusion
In summary, anomaly-based intrusion detection stands as a vital technology in modern cybersecurity strategies. Its capability to detect unforeseen threats by analyzing deviations from a baseline of normal behavior distinguishes it as an essential tool for defending against complex cyber attacks. While challenges exist in its implementation, such as ensuring accurate baseline establishment and managing computational demands, the benefits of deploying anomaly-based intrusion detection systems can far outweigh these challenges. As cyber threats evolve, the continuous development and refinement of these systems will be imperative to uphold secure and resilient digital environments, providing both real-time responses and foresight into future threat landscapes.