Introduction to the Comprehensive DLP Policy Framework
In today’s digital age, safeguarding data is paramount for organizations to protect against information breaches and ensure compliance with regulatory mandates. A comprehensive DLP policy framework serves as a critical instrument in this regard, offering structured processes and guidelines to secure sensitive data across various platforms. Implementing such a framework facilitates the prevention of unauthorized access, minimizing the risk of data loss and exposure. Fundamentally, these policies are meticulously crafted to tackle the myriad channels through which data breaches could potentially occur, be it email, cloud storage, or network transfers.
The primary objective of a comprehensive DLP policy framework is to set protocols that govern how data is accessed, shared, and retained. It encompasses both technological solutions and administrative measures, creating a holistic barrier against data breaches. Adopting a robust framework ensures that data handling procedures are not only efficient but also compliant with international standards and local regulations. Thus, enabling organizations to cultivate trust with stakeholders and gain a competitive advantage in the marketplace by showcasing their commitment to data security.
Moreover, a comprehensive DLP policy framework serves to educate and align personnel with the best practices in data management. Training and communication are integral components, empowering employees to recognize and mitigate risks promptly. Without such a framework, organizations expose themselves to the pitfalls of data mismanagement, which may lead to irreparable reputational damage and substantial financial losses. Consequently, implementing a comprehensive framework is not merely a reactive measure but a proactive strategy ensuring long-term security and operational resilience.
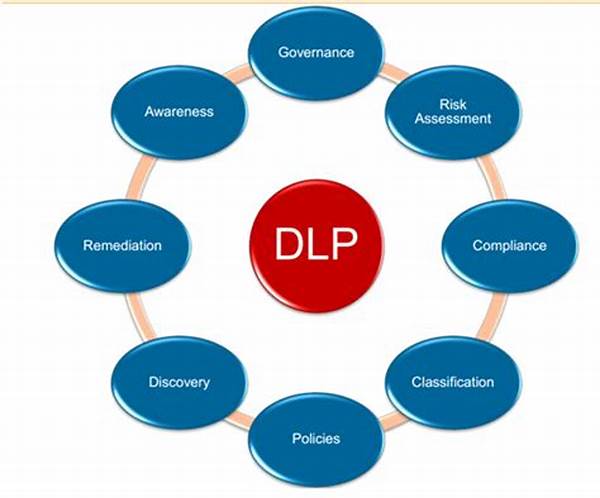
Key Components of a Comprehensive DLP Policy Framework
To establish a comprehensive DLP policy framework, organizations must first identify and classify sensitive data according to its importance and vulnerability. This crucial step allows for tailored protection measures that align with the organization’s specific requirements.
Next, the framework should integrate advanced technologies, such as encryption and access controls, to bolster data security. These technologies form the backbone of the organization’s defense strategies, ensuring that any data breaches are swiftly detected and addressed.
An effective comprehensive DLP policy framework requires continuous monitoring and threat assessment. By maintaining vigilance over data transactions and potential threats, organizations can promptly adjust their strategies to thwart emerging risks in the digital landscape.
Staff training underpins the success of any comprehensive DLP policy framework. Equipping employees with the knowledge and tools to adhere to security protocols minimizes human error, which is often a significant factor in data breaches.
Finally, regular audits and reviews of the comprehensive DLP policy framework ensure its relevance and effectiveness over time. This ongoing evaluation process enables organizations to remain adaptable in the face of evolving technological and regulatory changes.
Implementing a Comprehensive DLP Policy Framework
The implementation of a comprehensive DLP policy framework entails a systematic approach that begins with an assessment of existing data protection measures. Organizations must evaluate their current capabilities and identify gaps where security measures may be lacking or outdated. This initial step is vital to ensure that the new framework effectively addresses these deficiencies and aligns with the organization’s strategic objectives.
Subsequently, the design and execution of the framework must be undertaken with meticulous attention to detail. It involves not only deploying technological tools and protocols but also establishing a rigorous governance structure. A comprehensive DLP policy framework should define roles and responsibilities, creating an organized workflow for data protection activities. In doing so, organizations lay the groundwork for sustainable data security protocols that can withstand internal and external challenges.
Monitoring and Maintaining the Comprehensive DLP Policy Framework
Once the comprehensive DLP policy framework is in place, ongoing monitoring becomes essential to ensure its sustained effectiveness. This involves utilizing analytics and reporting tools to gather insights into data usage patterns and potential threats. By continuously analyzing these metrics, organizations can proactively refine their strategies to fortify defenses against emerging vulnerabilities.
Moreover, regularly reviewing and updating the framework is crucial for maintaining its relevance. Changes in the organizational environment or regulatory landscape may necessitate adjustments to policies and procedures. Regular audits and feedback loops enable organizations to adapt the comprehensive DLP policy framework in response to these dynamics, ensuring its continued efficacy and alignment with business goals.
Regulatory Compliance within a Comprehensive DLP Policy Framework
Regulatory compliance is a cornerstone of the comprehensive DLP policy framework. In an era marked by stringent data protection laws, organizations must adhere to legal mandates such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). This compliance is not merely about avoiding penalties; it represents a commitment to safeguarding stakeholder information.
In practice, a comprehensive DLP policy framework integrates compliance requirements into its core operations. It involves establishing protocols that ensure transparency and accountability in data handling processes. By doing so, organizations not only fulfill their legal obligations but also build trust with customers, partners, and other stakeholders.
Risk Management through a Comprehensive DLP Policy Framework
Risk management is a fundamental aspect enhanced by a comprehensive DLP policy framework. In today’s digital landscape, organizations face a myriad of threats, each posing unique challenges to data security. By implementing a structured framework, businesses gain the capability to identify, assess, and mitigate these risks effectively.
A comprehensive DLP policy framework enables organizations to establish risk management protocols that prioritize threats according to their potential impact. It provides guidelines for risk assessment and establishes mitigation strategies, such as the deployment of encryption technologies or the enforcement of stringent access controls. By proactively managing risks, an organization strengthens its resilience against data breaches and cyber-attacks, ultimately safeguarding its operations and reputation.
Summary of the Comprehensive DLP Policy Framework
In conclusion, a comprehensive DLP policy framework represents an essential strategy in the modern landscape of data protection. This framework combines technological solutions and administrative measures to create a robust barrier against data breaches. Through its structured protocols, it facilitates the secure handling and storage of sensitive information, aligning with both organizational goals and regulatory requirements.
Moreover, the comprehensive DLP policy framework emboldens organizations to address risk management proactively. By classifying data and employing advanced technologies, businesses can thwart potential threats before they escalate, thereby ensuring operational continuity and resilience. This proactive stance is underpinned by ongoing monitoring, assessment, and adaptation processes, which are vital to maintaining the framework’s relevance amid changing technological and regulatory contexts.
Implementing a comprehensive DLP policy framework is no longer an optional measure but a necessity for organizations committed to data integrity and stakeholder trust. It ensures that all aspects of data protection are meticulously managed, creating a secure environment that mitigates the risks associated with data breaches and unauthorized access. Ultimately, this framework is a testament to an organization’s dedication to safeguarding its most vital asset—its information.