In today’s digital age, the security of sensitive information has become a paramount concern for organizations across the globe. Cybersecurity protocols for sensitive information are designed to protect data from unauthorized access, disclosure, alteration, and destruction. These protocols are crucial in maintaining the integrity, confidentiality, and availability of information that—if compromised—could lead to significant financial and reputational damage. As cyber threats continue to evolve, it is imperative for businesses and individuals alike to implement robust cybersecurity measures aimed at safeguarding sensitive information.
Understanding Cybersecurity Protocols
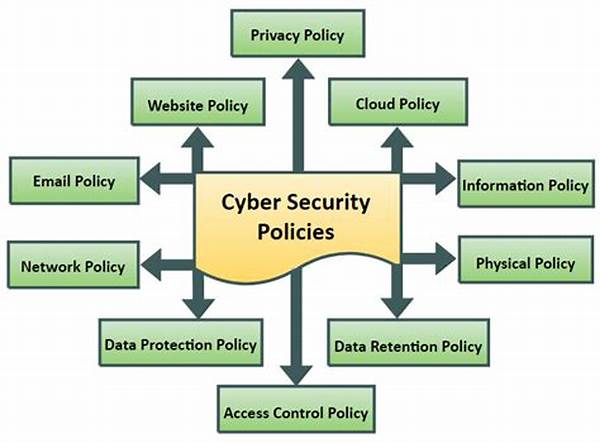
Cybersecurity protocols for sensitive information encompass a wide array of measures and procedures designed to protect data integrity against cyber threats. Implementation begins with identifying the types of sensitive information that require protection, such as personal data, financial records, and intellectual property. Once identified, organizations must enforce authentication protocols to ensure only authorized personnel can access sensitive information. Encryption is a fundamental aspect of cybersecurity protocols that ensures data in transit and at rest is protected from interception. Moreover, regular audits and monitoring are essential in detecting vulnerabilities and potential breaches; thereby, allowing timely intervention and mitigation of threats.
Training and awareness initiatives are integral components of cybersecurity protocols for sensitive information. Employees must be made aware of their roles and responsibilities in protecting sensitive data. Implementing a culture of security can significantly reduce the likelihood of human error, which is often the weakest link in cybersecurity defenses. By embracing comprehensive cybersecurity protocols, organizations are better equipped to face the myriad challenges posed by cyber threats, ensuring their sensitive information remains protected.
Key Components of Cybersecurity Protocols
1. Data Classification:
Cybersecurity protocols for sensitive information begin with classifying data according to its sensitivity and value. This classification guides the level of security measures required to protect different types of information.
2. Access Controls:
Implementing robust access controls is critical in ensuring only authorized individuals can access sensitive information. Cybersecurity protocols for sensitive information often include multi-factor authentication and role-based access controls.
3. Encryption:
Encryption is one of the most effective cybersecurity protocols for sensitive information, as it converts data into a ciphered form that can only be accessed by authorized parties with the proper decryption key.
4. Regular Audits:
Conducting thorough audits regularly is necessary to ensure that the cybersecurity protocols for sensitive information remain effective and adaptive against emerging threats through timely detection of vulnerabilities.
5. Incident Response Planning:
Developing an incident response plan is essential within cybersecurity protocols for sensitive information. It delineates the procedure for addressing security breaches, minimizing potential damage, and recovering compromised data.
Implementation Challenges
Despite the importance of cybersecurity protocols for sensitive information, organizations face various challenges in their implementation. One significant challenge is ensuring that these protocols keep pace with continuously evolving cyber threats. Cybercriminals are constantly devising new tactics to exploit vulnerabilities, making it necessary for security measures to adapt accordingly. Another challenge lies in balancing security with accessibility. While stringent protocols are necessary, they should not impede the day-to-day functions of users, which requires the development of user-friendly cybersecurity strategies.
Moreover, the wide adoption of remote work has introduced new complexities in implementing cybersecurity protocols for sensitive information. Remote work environments are often more vulnerable to cyber threats due to unsecured networks and devices. Overcoming these challenges necessitates a comprehensive approach that integrates technological solutions, employee training, and a commitment to continuous improvement in security measures. Organizations must invest in both technological resources and human capital to effectively implement and sustain cybersecurity protocols for sensitive information.
Measures to Enhance Protection
Organizations can employ several measures to enhance their cybersecurity protocols for sensitive information. Firstly, conducting risk assessments helps identify potential threats and vulnerabilities, allowing for customized security solutions. Continuous monitoring of information systems detects anomalies, thereby providing an early warning of potential breaches. Advanced technologies such as artificial intelligence and machine learning can enhance the effectiveness of cybersecurity protocols by identifying patterns and predicting future threats. Additionally, fostering a culture of security within the organization ensures that all members are actively involved in safeguarding sensitive information.
Education and training are indispensable in bolstering cybersecurity protocols for sensitive information. Regular instructional sessions can keep employees informed about the latest security threats and best practices. Furthermore, collaborating with external cybersecurity experts can provide organizations with additional insights and cutting-edge solutions. By integrating these measures, organizations can significantly strengthen their cybersecurity posture and ensure the protection of their sensitive information.
Influence of Regulations and Compliance
Various regulations and compliance requirements influence the deployment of cybersecurity protocols for sensitive information. Laws such as the GDPR and CCPA mandate specific security measures to protect personal data. Complying with these regulations is crucial, as non-compliance can result in severe financial penalties and reputational harm. These legal frameworks not only set standards for data protection but also provide organizations with guidelines to develop efficient cybersecurity protocols for sensitive information.
In response to regulatory demands, organizations often conduct compliance audits and adjust their protocols accordingly. While compliance with regulations ensures a baseline level of security, organizations should strive to exceed these minimum requirements. Adopting a proactive rather than reactive approach in adopting cybersecurity protocols for sensitive information ensures that organizations can anticipate threats and adapt to the evolving digital landscape, thereby safeguarding their critical data assets.
Evaluating the Impact of Cybersecurity Protocols
The impact of implementing comprehensive cybersecurity protocols for sensitive information is profound. By protecting against unauthorized access and data breaches, these protocols safeguard the organization’s intellectual property and sensitive data. This protection not only helps prevent financial loss but also fortifies the organization’s reputation. Clients and stakeholders are increasingly aware of cybersecurity issues, and a strong security posture can serve as a competitive advantage in the marketplace.
Moreover, effective cybersecurity protocols enhance an organization’s resilience against cyber threats. They enable organizations to respond swiftly and efficiently to incidents, minimizing disruption to operations. As a result, organizations are better positioned to maintain business continuity in the event of cyber-attacks. Therefore, investing in robust cybersecurity protocols for sensitive information is not merely a defensive measure but a strategic initiative that promotes long-term organizational stability and trust.