The increasing frequency and sophistication of insider threats pose significant concerns for organizations worldwide. As the digital landscape continues to evolve, fostering robust insider threat policies becomes a crucial aspect of organizational security strategy. Developing insider threat policies is not merely a reactive measure to emerging risks; rather, it integrates proactive multi-layered security approaches to safeguard sensitive information and assets. In this framework, comprehensive procedures are essential to detect, deter, and mitigate potential threats from within the organization.
Understanding Insider Threats
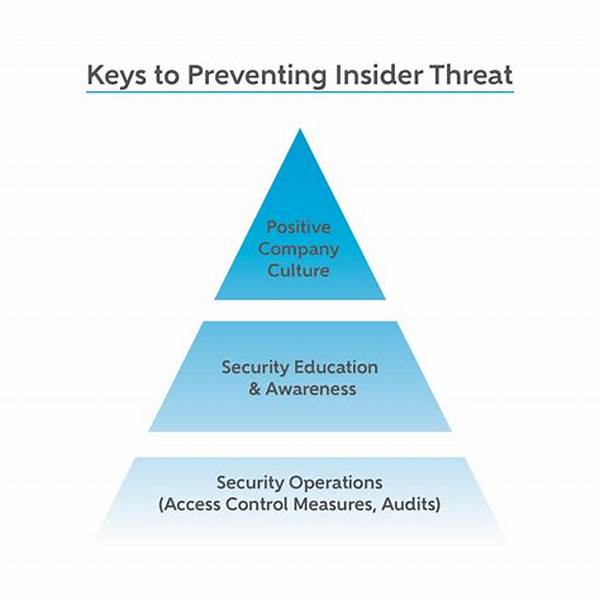
Developing insider threat policies requires a comprehensive understanding of the different types of insider threats an organization may face. These threats can be categorized into malicious insiders who intentionally breach security protocols, and negligent insiders whose lack of adherence inadvertently causes threats. Policies must be tailored to address both of these scenarios, ensuring that employees are both aware of the potentially devastating impacts of their actions and incentivized to uphold security measures. Providing ongoing education and creating a culture of responsibility are fundamental aspects of this approach, enabling an organizational environment where employees are vigilant against threats and motivated to report suspicious activities.
Furthermore, developing insider threat policies incorporates cutting-edge technology to enhance detection capabilities. By leveraging behavioral analytics and machine learning, organizations can identify subtle anomalies indicative of insider threats. These technologies provide vital insights which inform decision-making processes and empower security teams to act swiftly before breaches occur. This proactive stance not only minimizes risks but also fortifies the organization’s defenses against evolving threats. Ultimately, the incorporation of advanced technical solutions in developing insider threat policies enhances resilience and fosters trust across the enterprise.
Key Elements of Effective Policies
1. Risk Assessment: Conducting a thorough risk assessment is vital when developing insider threat policies. This process helps identify vulnerable areas and prioritize resources effectively.
2. Access Control: Implementing stringent access control measures ensures that only authorized personnel have access to sensitive data, mitigating the risk of unauthorized disclosures.
3. Employee Training: Training programs help employees understand the importance of security protocols, fostering a security-conscious organizational culture.
4. Incident Response Plan: A well-defined incident response plan enables organizations to quickly address breaches, minimizing damage and facilitating recovery.
5. Continuous Monitoring: Continuous monitoring of systems and personnel activities aids in early detection of potential insider threats, allowing prompt intervention.
Integrating Technological Solutions
In the modern era, developing insider threat policies necessitates the integration of technological solutions as a core component. Utilizing advanced monitoring systems and analytic tools is imperative to detect early warning signs of internal threats. These technologies can analyze vast volumes of data to identify patterns and anomalies, offering real-time insights into potential security breaches. By integrating technology into insider threat policies, organizations can significantly enhance their capacity for preemptive action, reducing the likelihood of critical information being compromised.
Moreover, developing insider threat policies with a technology-centric approach also involves implementing robust cybersecurity frameworks that adapt to current and anticipated threats. Cybersecurity technologies such as data encryption, identity verification systems, and automated alerts form the backbone of effective insider threat defenses. Together, these systems provide a comprehensive shield against potential threats, while ensuring compliance with regulatory standards. The strategic use of technology in policy development not only safeguards assets but also strengthens trust within the organization’s ecosystem.
Challenges in Policy Development
Developing insider threat policies is fraught with challenges that necessitate a nuanced approach. One of the most significant challenges is balancing security measures with employee privacy rights. Organizations must navigate the fine line between monitoring employee activities for security purposes and respecting individual privacy. Policies must clearly articulate the scope and intent of monitoring practices to maintain employee trust while safeguarding organizational assets.
Additionally, evolving threat landscapes further complicate policy development. As cyber threats become more sophisticated, insider threat policies must remain dynamic and adaptable. This requires constant evaluation and updating of policies to ensure they adequately address emerging risks. Organizations must also contend with resource constraints, as developing comprehensive policies often requires significant investment in technology, training, and personnel. Navigating these challenges demands astute leadership and a commitment to embedding security as an integral part of the organizational culture.
Steps to Reinforce Security Measures
Reinforcing security measures through developing insider threat policies entails a structured approach focusing on education, technology, and communication. Continuous education programs are pivotal in equipping employees with up-to-date knowledge on security best practices and the implications of potential threats. Regular training sessions and awareness campaigns should be integral segments of the policy, highlighting personal accountability and promoting vigilance among staff members.
Next, leveraging technology to automate and streamline security processes is crucial. Implementing advanced surveillance tools for real-time monitoring, establishing automated alert systems, and utilizing artificial intelligence for behavior pattern recognition are effective measures to detect suspicious activities promptly. These technological interventions, embedded within a well-constructed insider threat policy, significantly enhance the organization’s protective layers, guarding against internal misconduct and negligence.
Impact of Insider Threat Policies
The impact of robust insider threat policies extends beyond immediate security enhancements; it influences the overall organizational culture and operational efficiency. Developing insider threat policies that are comprehensive and well-communicated enhances employee engagement by fostering a sense of shared responsibility and awareness. Employees understand their roles in maintaining security and are more likely to actively participate in reporting potential threats.
Additionally, effective insider threat policies contribute to business continuity by reducing the risk of data breaches and operational disruptions. Organizations that prioritize developing insider threat policies can maintain a strong security posture, ensuring that sensitive data remains protected. Moreover, these policies demonstrate a commitment to security best practices, which can enhance the organization’s reputation and build confidence among stakeholders. Ultimately, well-formulated insider threat policies are instrumental in safeguarding the organization’s assets and promoting a culture of security.
Conclusion
In summary, developing insider threat policies is an essential undertaking for any organization striving to protect its interests in an increasingly complex threat environment. These policies require a multi-faceted approach, integrating risk assessments, employee training, technological solutions, and continuous monitoring to mitigate potential threats. While challenges exist in balancing security and privacy, as well as keeping pace with evolving threats, organizations can overcome these obstacles through effective leadership and a commitment to embedding security into the organizational ethos.
Developing insider threat policies not only bolsters an organization’s defense against potential threats but also fosters a culture of trust and accountability. By emphasizing education, leveraging technology, and maintaining clear communication, organizations can create an environment where employees are vigilant in safeguarding company assets. The lasting impact of these policies is a fortified security landscape, ensuring the organization’s resilience in today’s digital age.