In the contemporary digital landscape, the importance of authenticated data sources cannot be overstated. With data being at the core of decision-making processes across various sectors, ensuring the authenticity and integrity of this information is paramount. The seamless and secure facilitation of access to these data sources is an essential consideration for organizations looking to maintain competitive advantage and regulatory compliance. In this article, we will explore the multifaceted aspects of facilitating access to authenticated data sources.
Understanding the Importance of Authenticated Data Sources
Authenticated data sources are critical for ensuring that the information utilized in decision-making is both reliable and verifiable. From financial institutions to healthcare providers, diverse sectors rely on the integrity of data to guide strategic directions and operational actions. Facilitating access to authenticated data sources means creating pathways that allow for the seamless retrieval and validation of data without compromising security or privacy. By implementing robust authentication protocols, organizations can ensure that only authorized personnel have access to sensitive data, thereby safeguarding against potential breaches and data misuse. Moreover, facilitating access to authenticated data sources enhances transparency and accountability, fostering trust among stakeholders. This is essential in building sustainable relationships in an increasingly data-driven world. Proper facilitation thus acts as a cornerstone for establishing and maintaining the credibility of data accessed and applied within organizational ecosystems.
Strategies for Facilitating Access to Authenticated Data Sources
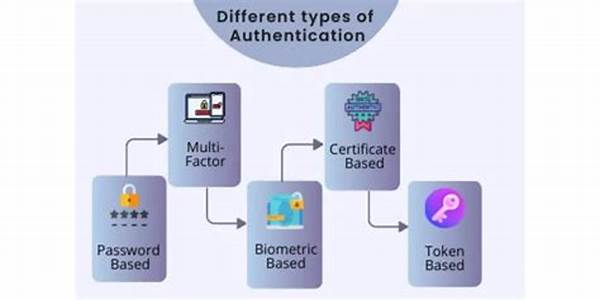
1. Authentication Protocols: Implementing multi-factor authentication and encryption enhances security, thereby facilitating access to authenticated data sources while ensuring data integrity.
2. User Management: Establishing precise user roles and permissions controls access, facilitating a smoother access to authenticated data sources for authorized users only.
3. Data Management Platforms: Employing sophisticated data management systems supports the facilitation of access to authenticated data sources by streamlining processes and documentation.
4. Compliance Standards: Adhering to international standards like GDPR and HIPAA ensures that the facilitation of access to authenticated data sources aligns with legal requirements.
5. Continuous Monitoring: Regular audits and monitoring of data access can facilitate access to authenticated data sources by identifying potential vulnerabilities swiftly.
Enhancing Data Security and Privacy
In an era where data breaches are increasingly common, enhancing data security and privacy is of utmost importance. Facilitating access to authenticated data sources is a critical step in this process. By ensuring that data is only accessible to authorized individuals, organizations can prevent unauthorized access and potential data breaches. Advanced encryption techniques and stringent access controls are fundamental components of a robust data security strategy. Additionally, continuous security assessments and adherence to compliance standards play a vital role in safeguarding data. By focusing on facilitating access to authenticated data sources, organizations can significantly mitigate the risks associated with data breaches and privacy violations. As a result, they can protect not only their own interests but also those of their stakeholders and customers.
Benefits of Facilitating Access to Authenticated Data Sources
Facilitating access to authenticated data sources brings numerous benefits to organizations globally. Reliable data access enhances decision-making processes, enabling informed strategic planning. Moreover, it builds trust with stakeholders, as accuracy and transparency are prioritized. Efficient data access also streamlines operations, reducing inefficiencies in data retrieval and processing. Additionally, compliance with regulatory standards becomes an attainable goal, ensuring organizations meet necessary legal requirements. Facilitating access to authenticated data sources ultimately contributes to the creation of resilient data ecosystems where information serves as a robust foundation for innovation and growth.
Challenges in Facilitating Access to Authenticated Data Sources
Despite the myriad benefits, facilitating access to authenticated data sources presents certain challenges. One of the primary concerns is maintaining the balance between accessibility and security. Organizations must ensure that access controls are sufficiently stringent to protect data, yet flexible enough to allow authorized personnel to perform necessary tasks. Additionally, the evolving nature of cybersecurity threats demands continuous updates to authentication protocols and security measures. Organizations must also address potential technical complexities and costs associated with implementing advanced data management systems. Facilitating access to authenticated data sources, while crucial, requires ongoing commitment and investment.
The Role of Technology in Facilitating Access
Technology plays a pivotal role in facilitating access to authenticated data sources. Advanced data management solutions provide the necessary tools for authentication, user management, and access control. Technologies such as blockchain and artificial intelligence offer innovative approaches to ensuring data integrity and security. Furthermore, cloud computing has transformed the way organizations store and access data, providing scalable solutions for managing large volumes of information. By leveraging these technological advancements, organizations can effectively facilitate access to authenticated data sources, enabling them to remain agile and responsive to changing market dynamics.
Conclusion
In conclusion, facilitating access to authenticated data sources is a complex yet essential process for organizations striving to thrive in today’s data-driven environment. By implementing robust security measures and leveraging technological advancements, organizations can safeguard data integrity and enhance decision-making capabilities. Despite the challenges, the benefits associated with authenticated data access are substantial, offering opportunities for improved efficiency, compliance, and stakeholder trust. As organizations continue to prioritize data security and privacy, the facilitation of access to authenticated data sources will remain a vital component of strategic planning and operational success.