In the contemporary business environment, safeguarding organizational assets against internal threats is of paramount importance. The specter of malicious insider activities has emerged as a critical concern for business entities, necessitating diligent efforts in risk assessment and management. Identifying malicious insider behaviors effectively involves understanding the multifaceted dimensions of human motives and technological vulnerabilities, thereby enabling companies to devise comprehensive security strategies that mitigate potential risks.
Understanding Insider Threat Dynamics
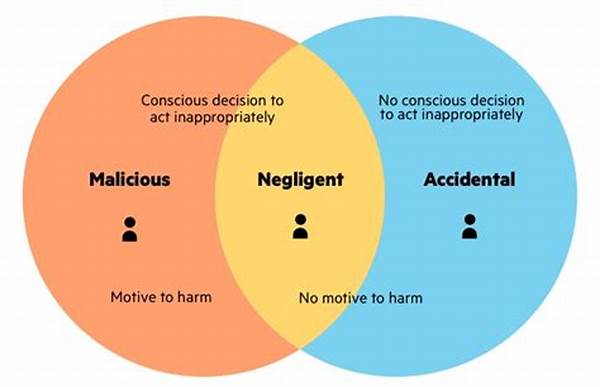
Identifying malicious insider behaviors necessitates a thorough comprehension of the varying intentions and actions associated with these threats. Insiders, who inherently possess organizational access and trust, can exploit their positions to compromise sensitive data, harm reputations, or execute financial fraud. Delving deep into behavioral patterns becomes imperative for preemptive detection and intervention.
The intricacies in distinguishing ordinary activities from malicious intent require an analytical approach. Behavioral anomalies, such as deviations from established work patterns or unauthorized access attempts, serve as potential red flags. Identifying malicious insider behaviors, therefore, hinges on the ability to evaluate these deviations within broader organizational contexts. By establishing a robust framework for monitoring and analysis, organizations can enhance their detection capabilities, thereby safeguarding vital assets and maintaining operational integrity.
Furthermore, a proactive mindset is instrumental in addressing insider threats. With technological advancements facilitating real-time monitoring and predictive analytics, organizations have the tools necessary to anticipate and neutralize potential threats. Ultimately, cultivating a culture of awareness and resilience is critical in supporting ongoing efforts to identify and counteract malicious insider behaviors effectively.
Key Indicators of Malicious Insider Behaviors
1. Access Patterns: Consistent monitoring of access logs can reveal discrepancies, aiding in identifying malicious insider behaviors through unauthorized data retrieval attempts and unusual login times.
2. Behavior Changes: Sudden shifts in an employee’s demeanor, such as increased secrecy or withdrawal, may indicate underlying issues contributing to malicious intent.
3. Data Transfer: Unexplained data transfers, particularly to unauthorized external devices, are pivotal in identifying malicious insider behaviors indicative of data exfiltration attempts.
4. System Manipulation: Attempted changes to system configurations or unauthorized installations can signal an insider’s malicious actions under the guise of routine maintenance tasks.
5. Peer Reports: Cultivating an environment where colleagues report suspicious activities can significantly enhance efforts in identifying malicious insider behaviors promptly and effectively.
Approaches to Mitigating Risks
Effective approaches to identifying malicious insider behaviors require an amalgamation of technological and human-centric strategies. Organizations should invest in advanced monitoring systems capable of tracking and analyzing user activities with precision. Such systems provide critical insights into potential anomalies, facilitating early detection and response mechanisms.
Moreover, fostering a transparent workplace culture is pivotal. Training sessions and workshops on data security and ethical conduct should be integral components of organizational policies. By engaging employees in these efforts, companies can build a collective understanding of security protocols and the significance of vigilance in identifying malicious insider behaviors. Consequently, enhanced awareness and a shared commitment to security cultivate a protective environment that deters insider threats from manifesting.
Technological Solutions in Detection
The employment of sophisticated technological solutions plays a vital role in identifying malicious insider behaviors. Cutting-edge tools like anomaly detection software and machine learning algorithms can analyze vast datasets, flagging deviations indicative of insider threats. Real-time alerts provide immediate notification, enabling organizations to swiftly mitigate emerging risks.
Integration of these solutions with existing security infrastructures creates a cohesive defense mechanism. Organizations can systematically assess potential vulnerabilities and streamline response strategies effectively. Consequently, the fusion of technology with human oversight equips businesses with comprehensive capabilities to address insider threats robustly, diminishing the likelihood of detrimental security breaches.
Comprehensive Security Strategies
Crafting a comprehensive security strategy is indispensable in the quest for identifying malicious insider behaviors. Building a robust cybersecurity framework requires collaboration across departments, ensuring alignment in threat management practices. This interdisciplinary approach fosters an atmosphere of trust and collective responsibility, crucial for maintaining organizational security.
Regular audits and risk assessments are foundational elements of a holistic security strategy. By evaluating existing protocols and identifying vulnerabilities, organizations can preemptively counteract potential threats. Consequently, this proactive stance not only strengthens defenses but also instills confidence among stakeholders regarding the organization’s commitment to safeguarding its assets.
Enhancing Employee Engagement
Engaging employees in security initiatives is instrumental in identifying malicious insider behaviors. Empowering individuals with knowledge and skills related to threat detection and prevention fosters a vigilant organizational culture. Tailored training programs and ongoing communication reinforce the importance of safeguarding sensitive information, aligning employee actions with corporate security objectives.
Furthermore, transparent dialogue between management and staff promotes a sense of ownership and accountability. By recognizing employees as critical allies in security, organizations benefit from diverse perspectives and insights, enhancing their ability to identify and mitigate insider threats. This collaborative effort ultimately bolsters the organization’s resilience against internal threats.
Summary
In summary, identifying malicious insider behaviors is a multifaceted endeavor requiring holistic strategies and vigilant monitoring. Understanding insider threat dynamics, characterized by behavioral anomalies and unauthorized activities, forms the foundation of detection efforts. By integrating technological solutions, such as machine learning and anomaly detection tools, organizations can enhance their ability to identify and respond to these threats in real time.
Furthermore, fostering a collaborative environment where employees are actively engaged in security practices strengthens the organization’s overall defense mechanisms. By building a culture of transparency and shared responsibility, businesses empower their workforce to recognize and report suspicious activities. Ultimately, the concerted efforts in identifying malicious insider behaviors contribute significantly to sustaining organizational integrity and trust, thereby safeguarding both company assets and stakeholder interests effectively.