In today’s interconnected digital landscape, the risk posed by insider threats is an imperative challenge for organizations across various sectors. These threats, originating from current or former employees, contractors, or business partners, can lead to severe data breaches, financial losses, and even reputational damage. The complexity of insider risks necessitates a robust strategy to mitigate potential harm. An Insider Threat Management Framework provides structured methodologies and tools to identify, assess, and neutralize such threats effectively before they manifest into significant damage.
Understanding the Insider Threat Management Framework
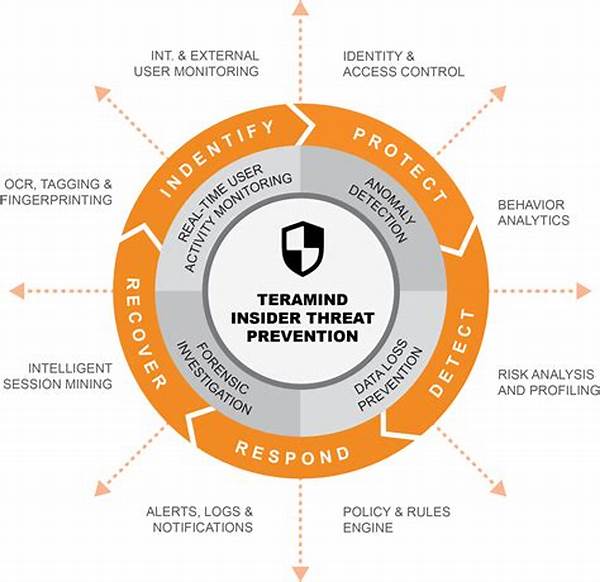
An Insider Threat Management Framework is a structured approach that organizations employ to detect, prevent, and respond to insider threats. This framework encompasses several components, including risk assessment, policy formulation, training, and technological solutions. Its primary aim is to safeguard an organization’s sensitive information and resources from misuse by individuals within the organization who may have legitimate access. By implementing a comprehensive insider threat management framework, businesses can proactively monitor and analyze employee behavior, effectively identifying any deviations from the norm that may indicate malicious intent. Through a combination of human analysis and automated systems, the framework allows organizations to establish a secure environment while maintaining trust among employees. Implementing such a framework not only protects an organization’s assets but also fosters a culture of security awareness and responsibility among its workforce.
Key Elements of a Robust Insider Threat Management Framework
1. Risk Assessment: Conduct thorough assessments to identify potential insider threat vectors, focusing on areas with high-risk potential within the organization.
2. Policy Development: Establish clear policies outlining acceptable employee behavior and protocols for reporting suspicious activities, supporting the insider threat management framework.
3. Training Programs: Develop and implement training programs aimed at educating employees on recognizing and reporting insider threats, integral to the insider threat management framework.
4. Technological Tools: Utilize advanced technologies such as monitoring software and anomaly detection systems to support the insider threat management framework.
5. Incident Response Plan: Design and frequently update a robust plan to respond to suspected insider threats, a crucial component of any insider threat management framework.
Implementing an Effective Insider Threat Management Framework
The application of an insider threat management framework involves a multifaceted approach to safeguard an organization against internal risks. Initially, conducting a comprehensive risk assessment is crucial for identifying vulnerabilities within the organization’s infrastructure. This assessment allows organizations to tailor their defense strategies effectively, prioritizing areas that require urgent attention. Subsequently, the development of a sound policy framework is essential. This inclusive policy should define clear guidelines for employee conduct, emphasizing transparency and accountability. Additionally, organizations should invest significantly in employee training programs aimed at raising awareness of insider threats and equipping staff with the knowledge to identify and report suspicious activities promptly. By integrating these components within an insider threat management framework, organizations can establish a proactive stance against potential insider risks and ensure prompt and appropriate responses to any incidents that occur.
Five Explanations of an Insider Threat Management Framework
1. An insider threat management framework enables organizations to detect early signs of malicious behavior by actively monitoring user activities and communications within the organization.
2. Data protection is paramount in an insider threat management framework, employing encryption and access controls to prevent unauthorized data access or leaks.
3. Regular audits and assessments are critical components of an insider threat management framework, ensuring continuous evaluation of policies and procedures for effectiveness and gaps.
4. Employee engagement in creating a vibrant security culture is a cornerstone of the insider threat management framework, promoting openness and trust within the organization.
5. Legal and regulatory compliance forms an integral part of any insider threat management framework, ensuring alignment with industry standards and government mandates to minimize legal risks.
Developing a Comprehensive Insider Threat Management Framework
A comprehensive insider threat management framework is pivotal in creating a secure and resilient organization. Designing this framework necessitates a balanced integration of policy, process, and technology to mitigate potential insider threats effectively. Initially, organizations must evaluate their current security posture and identify potential weaknesses that could be exploited by insider threats. This evaluation serves as the foundation for developing tailored security policies that define acceptable behaviors and establish clear protocols for employees. These policies should be communicated clearly to all members of the organization, fostering an environment of awareness and accountability. Furthermore, a critical component of this framework is the implementation of advanced technological solutions, including data loss prevention tools, behavioral analytics software, and robust access controls. These technologies enable continuous monitoring and detection of anomalies that may indicate insider threat activity, thereby enhancing the organization’s visibility into potential risks.
Critical Aspects of an Insider Threat Management Framework
Integrating a comprehensive insider threat management framework into an organization’s security posture is crucial for safeguarding sensitive assets and maintaining operational integrity. The success of this framework lies in its ability to balance rigorous security measures with the need to maintain a collaborative and trusting work environment. One critical aspect of this framework is the emphasis on training and communication. Organizations must invest in comprehensive training programs that educate employees on the importance of protecting sensitive information and recognizing potential threats. These programs should be reinforced with regular communication and awareness campaigns, keeping the topic of insider threats at the forefront of employees’ minds. Additionally, the development of an incident response plan is indispensable. This plan should outline precise steps to be taken in response to suspected insider threats, ensuring that the organization is prepared to respond swiftly and effectively to minimize potential damage. By incorporating these aspects into an insider threat management framework, organizations can establish a resilient security posture capable of mitigating risks and enhancing overall operational security.
Summary of the Insider Threat Management Framework
The insider threat management framework stands as a vital component in the contemporary security landscape, addressing the growing concerns associated with internal risks across organizations. This framework’s importance lies in its ability to systematically manage and mitigate threats posed by insiders who have legitimate access to sensitive organizational resources. At the core of this framework are diligent risk assessments, comprehensive policy development, and advanced technological implementations. By conducting thorough assessments, organizations can identify specific vulnerabilities and prioritize areas needing fortified defenses. A clearly defined policy outlines behaviors and reporting protocols, establishing expectations for employee conduct and fostering an atmosphere of vigilance.
Additionally, the integration of cutting-edge technologies within an insider threat management framework is instrumental in identifying suspicious activities early, allowing organizations to preempt potential incidents. Through continuous monitoring and data analysis, early indicators of insider threats can be detected, enabling timely interventions. Moreover, cultivating a security-conscious culture through ongoing training and communication is essential in maintaining organizational security and resilience. An effective insider threat management framework not only minimizes risks but also bolsters an organization’s capability to recover and respond to potential insider incidents promptly. Embracing this framework allows organizations to navigate the complexities of internal threats and uphold the integrity and security of their operational environment.