In today’s interconnected and digitalized environment, safeguarding organizations against insider threats has become a critical aspect of risk management. Insider threat risk management refers to the comprehensive methods employed to identify, assess, and mitigate threats posed by employees, contractors, or business associates with access to valuable information or systems. The increase in incidents involving insider threats necessitates a structured approach toward managing such risks, thereby ensuring organizational resilience and protective measures.
Understanding Insider Threat Risk Management
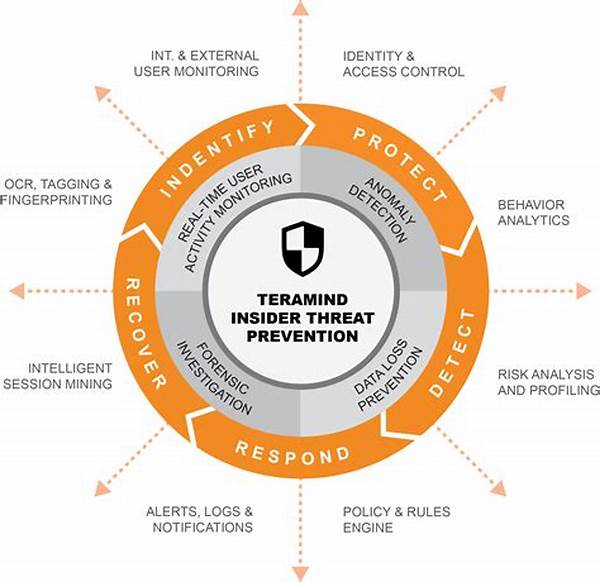
Insider threat risk management encompasses the implementation of strategies and processes that aim to protect the organization from internal actors who may potentially harm the entity. These threats can manifest as malicious attacks, unintentional errors, or negligence that lead to security breaches. Effective insider threat risk management requires a keen understanding of potential risks and proactive measures to curtail them. This involves not only technological solutions but also a focus on human behavior, organizational culture, and robust policies that govern access to sensitive data. By understanding the complexity of insider threats, organizations can better equip themselves to prevent security incidents and safeguard their assets.
Components of Effective Insider Threat Risk Management
1. Policy Development: Establish clear insider threat management policies, outlining expected behaviors and consequences of violations.
2. Access Control: Implement stringent access controls to minimize unauthorized access to sensitive information.
3. Behavioral Monitoring: Utilize monitoring systems to detect anomalies in employee behavior indicative of insider threats.
4. Employee Training: Conduct regular training sessions to ensure employees understand the importance of security protocols.
5. Incident Response Planning: Develop and maintain an incident response plan tailored to manage potential insider threat scenarios.
The Role of Technology in Insider Threat Risk Management
Technological advancements play a pivotal role in the framework of insider threat risk management. Tools such as data loss prevention (DLP) software, user and entity behavior analytics (UEBA), and identity and access management (IAM) systems are integral to monitoring and mitigating insider threats. These technologies not only enable organizations to detect and respond to suspicious activities in real-time but also help in analyzing patterns that may indicate potential risk. By leveraging these technologies, organizations can bolster their security posture and enhance their insider threat risk management capabilities, thereby minimizing the likelihood of data breaches or intellectual property theft from internal sources.
Cultural and Ethical Considerations in Insider Threat Risk Management
The human element is a significant factor in insider threat risk management. Cultivating a security-conscious corporate culture is essential, where employees understand the ethical implications of their actions concerning data security. This includes fostering an environment of trust, transparency, and accountability. Providing channels for employees to report suspicious activities without fear of retribution is a critical factor in this endeavor. Balancing the need for security with respect for employee privacy rights is essential, ensuring that insider threat detection measures do not infringe on individual privacy while still maintaining organizational security.
Legal and Regulatory Aspects of Insider Threat Risk Management
Compliance with legal and regulatory requirements is an imperative aspect of insider threat risk management. Organizations must navigate a complex landscape of regulations governing data protection and privacy, such as the General Data Protection Regulation (GDPR) or industry-specific guidelines. Staying abreast of these regulations ensures that insider threat management practices are not only effective but also legally sound. This alignment with legal standards mitigates the risk of legal repercussions, thereby safeguarding the organization from potential sanctions or fines that could arise from non-compliance.
Psychological Aspects of Insider Threat Risk Management
Understanding the psychological factors that may influence insider behaviors is crucial for effective insider threat risk management. Psychological assessments and profiling can help identify individuals who may pose a risk due to stress, dissatisfaction, or other personal issues. These insights allow for targeted interventions, which may include counseling or support programs. An awareness of these psychological dimensions adds an extra layer of preventive measure within an organization’s risk management strategy, ensuring that potential threats are addressed proactively before they materialize into actual breaches.
Conclusion
In conclusion, insider threat risk management is an essential component of modern organizational security strategies. By deploying a combination of policy enforcement, technological solutions, cultural transformation, and legal adherence, organizations can create a robust defense against insider threats. The multifaceted nature of insider threats necessitates a comprehensive approach that considers technical, human, and regulatory dimensions. Ensuring a sustainable insider threat risk management plan involves continuous evaluation and adaptation to emerging risks, thereby safeguarding the organization’s assets and maintaining trust with stakeholders.