In the ever-evolving landscape of digital security, the demand for innovative and effective solutions continues to rise. Enter the realm of lightweight cybersecurity threat devices, which are designed to provide robust protection against potential digital threats while maintaining a minimal footprint. As cyber threats become more sophisticated, the importance of these devices in safeguarding critical information and maintaining the integrity of information systems cannot be understated. Lightweight cybersecurity threat devices offer an efficient means to enhance security measures without compromising performance or efficiency, making them an essential component of modern cybersecurity strategies.
The Importance of Lightweight Cybersecurity Threat Devices
Lightweight cybersecurity threat devices are essential in today’s digital age due to their ability to deliver effective security without taxing system resources. These devices are built to detect and neutralize threats swiftly, ensuring that critical infrastructures remain uncompromised. Their lightweight nature means they can be deployed across various platforms, from personal computers to large-scale networks, without affecting overall performance. The strategic integration of these devices into existing security frameworks can significantly enhance the resilience of information systems against a wide array of cyber threats, thereby providing peace of mind to organizations and individuals alike.
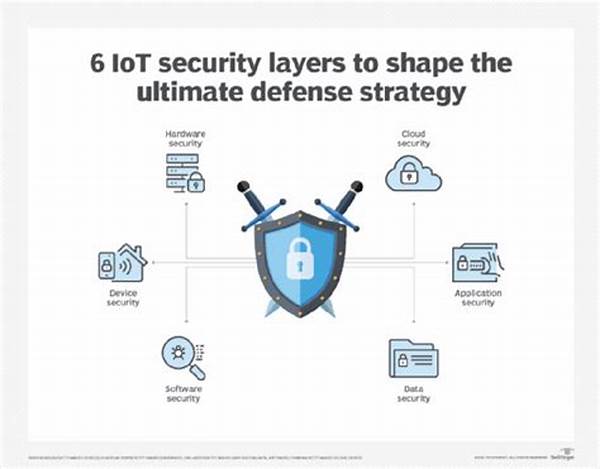
Moreover, the adaptability of lightweight cybersecurity threat devices enables them to respond promptly to the dynamic nature of cyber threats. As malicious actors continually develop new techniques to breach security, these devices serve as a frontline defense, offering proactive measures to counteract emerging risks. With the ever-increasing number of connected devices and the expansion of the Internet of Things (IoT), the necessity for these lightweight tools is more prominent than ever. The ability to provide comprehensive protection without inducing system lag is a hallmark of their efficiency.
Key Characteristics of Lightweight Cybersecurity Threat Devices
1. Efficiency: Lightweight cybersecurity threat devices are designed to perform efficiently, ensuring security measures do not hinder operational capabilities.
2. Adaptability: These devices can easily adapt to new threats, thanks to continuous updates and advanced algorithms that enhance their detection capabilities.
3. Versatility: Deployable across various environments, lightweight cybersecurity threat devices serve multiple platforms, from personal setups to enterprise networks.
4. Cost-Effectiveness: Offering high performance without significant investment makes these devices a cost-effective choice for organizations of all sizes.
5. User-Friendly Interface: Simplified interfaces ensure that even non-experts can manage these devices with great effectiveness, reducing the need for extensive training.
Integration of Lightweight Cybersecurity Threat Devices
The seamless integration of lightweight cybersecurity threat devices into existing networks is a critical aspect of their deployment. These devices are engineered to fit into multiple network topologies without requiring extensive modifications. Through advanced threat detection and mitigation capabilities, these devices play a vital role in strengthening the cybersecurity posture of organizations. They ensure that sensitive data remains protected from potential breaches, thus maintaining the confidentiality, integrity, and availability of information.
Furthermore, lightweight cybersecurity threat devices often include features that allow for comprehensive monitoring of network activity. This enables security personnel to identify and address vulnerabilities promptly, preventing potential exploits. By providing real-time alerts and detailed analytics, these devices empower organizations to take proactive measures against cyber attacks. Their integration is particularly vital in environments requiring high levels of security, such as financial institutions, healthcare sectors, and governmental bodies.
Benefits and Challenges of Lightweight Cybersecurity Threat Devices
Deploying lightweight cybersecurity threat devices comes with notable advantages, such as improved security without significant resource utilization. Their small footprint ensures minimal impact on system performance while providing comprehensive threat detection capabilities. However, challenges in integrating these devices can arise, particularly in environments with diverse and complex IT infrastructures. Compatibility and interoperability are essential factors to consider during implementation.
Additionally, the ongoing need for updates and maintenance can be a challenge for organizations utilizing lightweight cybersecurity threat devices. Despite their minimalistic design, these devices require continual improvements to counteract evolving threats, necessitating resources and planning. Nevertheless, the benefits provided by these devices in enhancing security measures make them a valuable investment for modern digital ecosystems.
Deployment Strategies for Lightweight Cybersecurity Threat Devices
Strategically deploying lightweight cybersecurity threat devices is crucial to maximizing their effectiveness. Establishing a comprehensive deployment plan involves understanding the specific security needs of an organization and identifying potential risks. By conducting a thorough risk assessment, organizations can pinpoint areas where lightweight devices will have the most impact. This targeted approach ensures optimal protection and resource utilization.
Moreover, ongoing evaluation and adjustment of security protocols are imperative to address new threats as they arise. Organizations must maintain vigilance, continuously assessing the performance of lightweight cybersecurity threat devices and integrating new technologies as needed. By fostering a proactive security culture, organizations can better protect themselves against the ever-evolving landscape of digital threats.
Future Prospects of Lightweight Cybersecurity Threat Devices
The future of lightweight cybersecurity threat devices is promising, given the continuous advancements in technology and the increasing sophistication of cyber threats. As artificial intelligence and machine learning become more embedded in cybersecurity solutions, these devices are expected to become even more efficient in anticipating and mitigating potential risks. The ability to learn from past incidents and apply that knowledge to prevent future breaches positions lightweight cybersecurity threat devices as a crucial element in the fight against cybercrime.
The growing interconnectivity of devices further underscores the necessity of lightweight solutions. As the adoption of IoT devices expands, the demand for efficient, adaptable, and robust cybersecurity measures becomes imperative. Lightweight cybersecurity threat devices are well-positioned to meet these needs, offering scalable solutions that cater to a wide array of digital environments. Their continued evolution will undoubtedly play a significant role in shaping the future of cybersecurity, safeguarding organizations and individuals from emerging threats.
Summary
In summation, lightweight cybersecurity threat devices represent a pivotal component in the modern cybersecurity framework. By delivering efficient and adaptable solutions, these devices meet the complex security needs of contemporary digital environments. Their strategic deployment provides organizations with a robust defense against potential threats, ensuring the protection of sensitive data and the uninterrupted operation of critical systems.
As cyber threats continue to evolve, the necessity for lightweight cybersecurity threat devices becomes increasingly apparent. These devices not only offer a favorable cost-to-performance ratio but also support strategic security objectives by providing enhanced threat detection and response capabilities. Consequently, their adoption is anticipated to grow, affirming their role as indispensable tools in the ever-evolving landscape of cybersecurity.