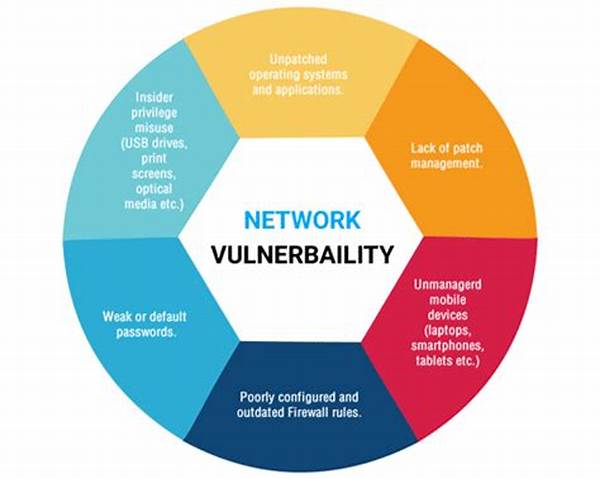
In the contemporary digital landscape, a comprehensive understanding of network vulnerabilities is pivotal for safeguarding information integrity and security. Network vulnerability analysis applications emerge as quintessential tools that provide insights into potential threats and weaknesses within an IT infrastructure. This article will elucidate various aspects and functionalities of network vulnerability analysis applications, highlighting their indispensability in modern cybersecurity strategies.
Understanding Network Vulnerability Analysis Applications
Network vulnerability analysis applications are specialized software solutions designed to identify, assess, and mitigate vulnerabilities within network systems. These applications play a critical role in cybersecurity by scanning networks for potential threats, weak points, and misconfigurations that may jeopardize system integrity. By employing a variety of analytical techniques, these applications offer organizations a proactive measure to enhance their security postures.
The primary objective of network vulnerability analysis applications is to provide a comprehensive overview of an organization’s network security status. This involves detailed assessments that identify vulnerabilities, categorize their severity, and recommend appropriate remediation measures. These applications enable IT teams to prioritize their response efforts efficiently, ensuring critical vulnerabilities are addressed promptly to mitigate risks.
Moreover, network vulnerability analysis applications are integral in ensuring compliance with various regulatory standards and industry best practices. By regularly conducting vulnerability assessments, organizations demonstrate due diligence in maintaining secure networks and protecting sensitive data. Thus, these applications are indispensable for enterprises striving to achieve cybersecurity resilience and maintain trust with stakeholders.
Key Features of Network Vulnerability Analysis Applications
1. Network vulnerability analysis applications offer real-time scanning capabilities, allowing organizations to identify vulnerabilities as they arise, thereby enabling timely intervention and mitigation.
2. These applications provide detailed reporting and analytics features, facilitating the evaluation of security posture and aiding in strategic decision-making for cybersecurity enhancements.
3. They support automation in vulnerability management, reducing manual efforts and ensuring consistent and comprehensive monitoring of network infrastructures.
4. Network vulnerability analysis applications integrate with other cybersecurity tools and platforms, enhancing the overall security ecosystem and fostering a holistic approach to threat management.
5. Customization options in network vulnerability analysis applications allow organizations to tailor assessment parameters based on specific security policies and infrastructure requirements.
The Importance of Network Vulnerability Analysis Applications
Network vulnerability analysis applications are paramount in identifying potential threats that could exploit vulnerabilities within an organization’s digital ecosystem. By utilizing advanced scanning techniques, these applications offer a proactive measure in maintaining robust cybersecurity defenses. They also help in cultivating a security-conscious culture among employees by highlighting the significance of regular vulnerability assessments.
Furthermore, these applications play a crucial role in incident response planning. By understanding possible vulnerabilities, organizations can devise realistic threat scenarios and establish effective response strategies. Network vulnerability analysis applications thus form a foundational element in the overall risk management framework, allowing organizations to adapt swiftly to the evolving threat landscape.
The continuous advancement of network vulnerability analysis applications equips organizations with the ability to stay ahead of potential cyber threats. With the increasing sophistication of cyber-attacks, the ongoing adaptation and upgrading of these applications are essential in maintaining resilient security postures. Consequently, investing in these applications is a significant step toward ensuring the long-term security and sustainability of organizational operations.
Components of Network Vulnerability Analysis Applications
A comprehensive network vulnerability analysis application typically comprises several integral components designed to deliver thorough assessments. These components include scanning engines that identify potential vulnerabilities, databases that maintain updated information on known vulnerabilities, and analytical tools that assess and prioritize risks. Additionally, reporting modules provide detailed insights and recommendations for remedial actions.
Network vulnerability analysis applications are consistently updated to address the evolving nature of cyber threats. Integration with global threat intelligence feeds ensures these applications are informed of emerging vulnerabilities and potential zero-day threats. This proactive updating mechanism is essential to providing reliable and current vulnerability assessments.
User interface design is another critical component of network vulnerability analysis applications, facilitating ease of use and efficient navigation for IT teams. A well-designed interface supports quick identification of vulnerabilities and simplifies the management and response processes. Therefore, the user interface plays a pivotal role in enhancing the overall experience and efficacy of these applications.
Advancements in Network Vulnerability Analysis Applications
Innovations in network vulnerability analysis applications drive significant advancements in their capabilities, incorporating machine learning and artificial intelligence to enhance threat detection. These technologies enable applications to predict potential vulnerabilities and adapt their assessments to evolving cyber threats, thus delivering more accurate and proactive security insights.
Moreover, the integration of cloud-based solutions has diversified the application landscape, providing scalable and accessible security assessments. Cloud-based network vulnerability analysis applications allow for seamless updates and extensive data aggregation, empowering organizations with real-time vulnerability insights across distributed network environments. This transition to cloud platforms signifies a critical leap in achieving comprehensive, efficient, and cost-effective security solutions.
The trend toward automated vulnerability analyses reflects the industry’s shift toward proactive cybersecurity measures. Automation within network vulnerability analysis applications reduces human error, expedites threat detection processes, and ensures continuous monitoring, all while maintaining adherence to stringent security standards.
Overcoming Challenges with Network Vulnerability Analysis Applications
Despite their myriad benefits, network vulnerability analysis applications face challenges such as adapting to diverse IT environments and addressing unique organizational needs. Tailoring applications to meet specific security policies and infrastructure configurations requires careful customization and integration efforts. Overcoming these challenges is fundamental to achieving optimal performance and maximizing the potential of these applications.
Furthermore, organizations must address the challenge of balancing automated analyses with human oversight. While network vulnerability analysis applications excel in identifying threats, strategic human intervention remains crucial in interpreting results and making informed decisions. Effective collaboration between technology and personnel ensures vulnerabilities are addressed with precision and awareness of broader security implications.
Organizations must also navigate the complexities of ensuring data privacy and safeguarding sensitive information during vulnerability assessments. Network vulnerability analysis applications must be designed with robust security measures to protect assessment data against unauthorized access and potential breaches, thereby maintaining data integrity and confidentiality.
Summary of Network Vulnerability Analysis Applications
In summary, network vulnerability analysis applications are indispensable tools in the realm of cybersecurity, facilitating the identification and mitigation of potential threats across digital infrastructures. These applications provide comprehensive assessments, allowing organizations to prioritize and address vulnerabilities, thereby enhancing their overall security posture. The strategic implementation of these applications ensures proactive defense mechanisms that align with evolving cyber threats.
The consistent evolution of network vulnerability analysis applications empowers organizations to maintain resilience against increasingly sophisticated cyber-attacks. With advancements in machine learning and cloud technologies, these applications deliver agile and comprehensive security solutions that are critical for safeguarding sensitive data and ensuring regulatory compliance. By leveraging these applications, organizations not only protect their digital assets but also cultivate a culture of security literacy and vigilance among their workforce.