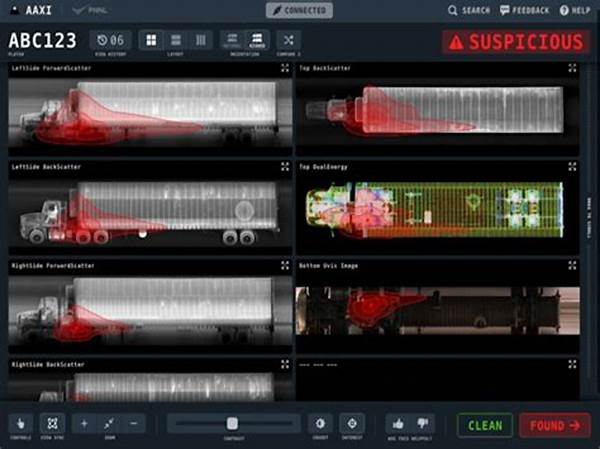
In the ever-evolving landscape of technological advancements, the significance of security cannot be overstated. Ensuring the safety of information and infrastructure remains a paramount concern for organizations worldwide. Non-intrusive security monitoring technology emerges as a revolutionary solution designed to address these concerns effectively. This technology facilitates comprehensive oversight of security infrastructure without infringing on the operational efficiency of systems.
Understanding Non-Intrusive Security Monitoring Technology
Non-intrusive security monitoring technology serves as a sophisticated method to safeguard assets while ensuring minimal disruption to system performance. It leverages advanced algorithms and analytics to provide real-time insights and alerts on potential security threats. This technology operates seamlessly across networks, ensuring continuous monitoring and immediate response to anomalies. Unlike traditional intrusive methods, it ensures that system functionalities remain unaffected, thereby promoting an uninterrupted workflow. Organizations are progressively gravitating towards this technology, recognizing its capacity to provide robust security without the drawbacks associated with traditional monitoring systems.
Incorporating non-intrusive security monitoring technology into an organization’s security architecture fosters an environment where security and efficiency coexist harmoniously. By enabling real-time monitoring and analysis, it empowers organizations to preemptively identify and neutralize threats. This proactive approach significantly reduces the risk of unauthorized access and data breaches, securing organizational data assets. As the demand for enhanced security solutions intensifies, non-intrusive security monitoring technology stands out as an indispensable tool, influencing the future trajectory of security strategies across various sectors.
Key Features of Non-Intrusive Security Monitoring Technology
1. Non-intrusive security monitoring technology offers real-time monitoring capabilities, enabling organizations to detect threats instantly without affecting system operations.
2. The technology integrates seamlessly with existing infrastructure, ensuring a smooth transition and sustained functional efficiency.
3. Advanced analytical tools embedded within non-intrusive security monitoring technology provide comprehensive insights into potential threats, facilitating timely interventions.
4. Its unobtrusive nature ensures that the workflow remains uninterrupted, thereby fostering operational continuity.
5. By leveraging innovative algorithms, it minimizes false alarms, enhancing the accuracy of threat detection processes.
Advantages of Non-Intrusive Security Monitoring Technology
Non-intrusive security monitoring technology presents myriad advantages that contribute to its growing adoption in diverse sectors. This technology embodies a strategic approach to cybersecurity, emphasizing the preservation of operational efficiency. One of the prominent benefits lies in its ability to function without impacting the normal operations of an organization’s IT infrastructure. This is paramount in environments where downtime or performance degradation is unacceptable.
Furthermore, the non-intrusive nature of the technology allows for continuous, real-time monitoring, which is critical in promptly identifying and addressing potential security threats. The analytics capabilities, empowered by machine learning algorithms, facilitate the detection of anomalies that may signal security breaches, thereby enabling timely interventions. This proactive defense mechanism substantially mitigates the risk of data breaches and unauthorized access, ensuring the robust protection of sensitive information. As the demand for reliable and efficient security solutions escalates, the advantages attributed to non-intrusive security monitoring technology reinforce its status as a pivotal component in the cybersecurity domain.
Implementing Non-Intrusive Security Monitoring Technology
Implementing non-intrusive security monitoring technology involves a thorough assessment of an organization’s existing security framework. It necessitates a methodical approach, beginning with the identification of specific security needs and vulnerabilities. Once identified, the integration of the technology is executed meticulously to ensure harmonious alignment with current systems.
Critical to this implementation process is the selection of appropriate tools and platforms that complement the organization’s security objectives. Following integration, continuous assessment and optimization are imperative to adapt to evolving threats. The process, while demanding, culminates in fortified security measures that offer comprehensive protection without disrupting organizational productivity. By prioritizing non-intrusive security monitoring, organizations uphold a robust, adaptive security posture capable of withstanding the complexities of modern cyber threats.
The Future of Non-Intrusive Security Monitoring Technology
The trajectory of non-intrusive security monitoring technology foresees an era where security measures are synonymous with seamless operational performance. As technological advancements continue to unfold, this technology promises to evolve correspondingly, integrating enhanced features that cater to the dynamic nature of security challenges.
Continued innovation in non-intrusive monitoring technology will likely include more advanced machine learning capabilities, providing even greater precision in threat detection and prevention. This evolution will underscore its efficacy as an indispensable tool in comprehensive security strategies, transforming the landscape of cybersecurity. Organizations that prioritize the adoption of this technology position themselves at the forefront of security innovations, ensuring their resilience in an increasingly complex digital environment.
Challenges and Considerations in Adoption
While non-intrusive security monitoring technology offers unparalleled benefits, it is not devoid of challenges. The primary consideration revolves around the initial investment costs associated with acquiring and integrating this advanced technology. Organizations must evaluate the cost-benefit ratio to ensure that the long-term advantages outweigh initial expenditures.
Another consideration is the ongoing need for updating and optimizing these systems to keep pace with emerging threats and vulnerabilities. This requires a dedicated team of cybersecurity professionals, underscoring the importance of investing in skills development and training. Despite these challenges, the strategic implementation of non-intrusive security monitoring technology can yield substantial returns by fortifying an organization’s security framework and safeguarding critical data assets.
Conclusion: The Impact of Non-Intrusive Security Monitoring Technology
In conclusion, non-intrusive security monitoring technology represents a groundbreaking advance in the domain of cybersecurity, characterized by its ability to provide robust protection without compromising system functionality. This technology facilitates a proactive approach to threat detection and mitigation, empowering organizations to maintain the confidentiality, integrity, and availability of their data.
By offering continuous, real-time monitoring and integrating seamlessly into existing security architectures, non-intrusive security monitoring technology addresses the critical need for efficient security solutions in today’s digital world. As organizations increasingly seek out innovative methods to protect their assets, the adoption of this technology signifies a significant step toward achieving comprehensive, integrated security measures that are both effective and unobtrusive.