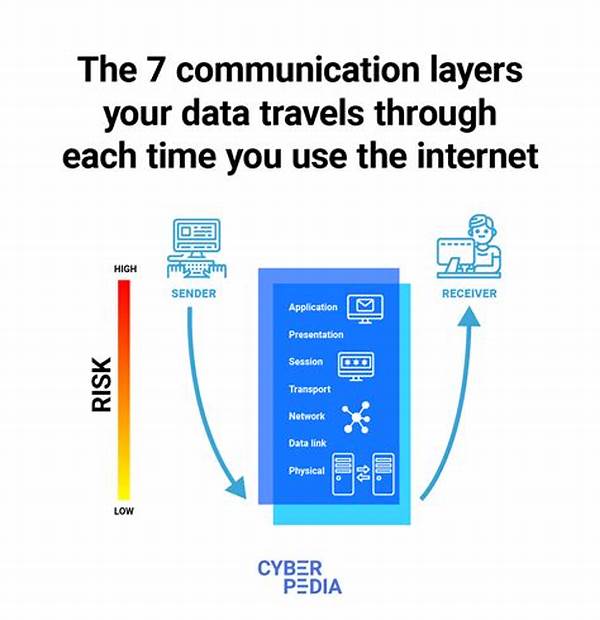
In the contemporary digital landscape, safeguarding data access has become imperative due to the increasing prevalence of cyber threats. Secure data access protocols play a pivotal role in ensuring that sensitive information remains protected from unauthorized access and breaches. By implementing these protocols, organizations can maintain the integrity, confidentiality, and availability of their data, which are the cornerstones of robust cybersecurity measures. The implementation of these protocols is essential across various sectors, including finance, healthcare, and government, where sensitive data transmission is routine. Understanding the significance of secure data access protocols is crucial for businesses aiming to protect their digital assets.
Importance of Secure Data Access Protocols
The implementation of secure data access protocols is vital in safeguarding sensitive information from cyber threats. These protocols ensure that data is accessed only by authorized individuals, thus maintaining confidentiality. Furthermore, they protect data integrity by preventing unauthorized alterations. By utilizing encryption methods, secure data access protocols ensure that data remains unreadable to unauthorized users. Additionally, these protocols help in auditing and monitoring access attempts, thus enhancing accountability. Organizations adopting secure data access protocols not only protect their data but also build trust with their clients and stakeholders, fostering long-term business relationships.
Secure data access protocols are crucial for maintaining data integrity, ensuring that only authorized personnel can view or modify sensitive data. These protocols employ encryption, authentication, and authorization measures to safeguard data. By implementing these measures, organizations decrease the risk of data breaches. Moreover, these protocols facilitate compliance with data protection regulations, enhancing organizational credibility. Furthermore, they aid in the recovery of data in case of unexpected incidents, reducing potential downtimes. These benefits underscore the significance of secure data access protocols in the contemporary digital environment.
Key Elements of Secure Data Access Protocols
1. Encryption Standards: Secure data access protocols heavily rely on encryption to protect sensitive information during transmission and storage. This ensures that even if data is intercepted, it remains unreadable without the proper decryption keys.
2. Authentication Mechanisms: These protocols implement robust authentication processes, verifying the identities of users accessing the data. Multi-factor authentication is a common method used to enhance security.
3. Access Control: Secure data access protocols enforce strict access control measures. They grant permissions based on user roles, ensuring that only authorized personnel have access to specific data sets.
4. Audit Trails: Maintaining detailed logs of data access attempts is essential. These logs enable organizations to monitor and review access patterns, facilitating the identification of unauthorized attempts.
5. Compliance and Regulations: Secure data access protocols ensure compliance with regulations such as GDPR, HIPAA, and others, helping organizations avoid legal repercussions and enhance their reputation.
Challenges in Implementing Secure Data Access Protocols
Organizations face several challenges while implementing secure data access protocols. The complexity of these protocols can be daunting, requiring significant resources and expertise. Adequate training and awareness among employees are crucial to ensure adherence to these protocols. Additionally, balancing security with usability presents challenges, as overly stringent protocols might impede productivity. Organizations must navigate these challenges to achieve an optimal balance. Furthermore, continually evolving cyber threats necessitate constant updates and reviews of existing protocols to ensure their efficacy. These hurdles highlight the need for a strategic approach in implementing secure data access protocols.
Data breaches and cyber threats are evolving rapidly, compelling organizations to constantly adapt their security measures. Implementing secure data access protocols is not a one-time effort but requires ongoing monitoring and adjustments. Regularly updating security measures to counteract new threats is essential for maintaining data integrity. Moreover, integrating these protocols with existing IT infrastructure can pose compatibility issues. Organizations must address these compatibility challenges to ensure seamless operations. Solving these challenges is fundamental to the successful implementation of secure data access protocols, ensuring long-term data security.
Technologies Supporting Secure Data Access Protocols
Current technologies significantly enhance secure data access protocols. Encryption technologies are continuously advancing, providing stronger protection against data breaches. Similarly, blockchain technology offers decentralized and immutable record-keeping, enhancing data security. Identity and Access Management (IAM) systems provide comprehensive solutions for managing user identities and regulating access efficiently. Additionally, Artificial Intelligence (AI) and Machine Learning (ML) are increasingly used to predict and prevent unauthorized access attempts by recognizing unusual patterns. These technologies collectively support the implementation of secure data access protocols, ensuring their effectiveness in protecting sensitive information.
The integration of advanced technologies into secure data access protocols strengthens their efficacy. By harnessing AI and ML, organizations can automate threat detection, identifying potential vulnerabilities swiftly. Furthermore, next-generation firewall systems provide enhanced network security, adding an additional layer of protection. Cloud-based security solutions offer scalable options, catering to the dynamic needs of businesses. As technology evolves, organizations must leverage these advancements to fortify their secure data access protocols. These technological developments facilitate the creation of robust security architectures, essential for protecting critical data assets.
Metrics for Evaluating Secure Data Access Protocols
Evaluating the effectiveness of secure data access protocols is vital for ensuring data protection. Key metrics include the number of unauthorized access attempts, response times to potential threats, and the rate of compliance with regulations. Monitoring these metrics allows organizations to identify areas for improvement and adjust their protocols accordingly, enhancing overall security. Additionally, user feedback on accessibility and usability provides insights into the effectiveness of these protocols. Conducting regular security audits and assessments ensures that protocols remain up-to-date with evolving threats. By assessing these metrics, organizations can maintain high standards of data security.
Maintaining effective secure data access protocols requires continuous evaluation. Regular assessments help determine protocol efficiency and identify potential weaknesses. Key performance indicators such as incident response times and audit trail completeness offer valuable insights. Additionally, the frequency of security incidents can indicate the robustness of existing protocols. Feedback from system users on access controls and overall usability contributes to ongoing improvements. Frequent evaluations are pivotal in adapting secure data access protocols to the ever-changing digital landscape.
Future Trends in Secure Data Access Protocols
As technology continues to advance, secure data access protocols are expected to evolve significantly. Trends indicate a shift towards zero-trust architectures, emphasizing thorough verification of users and devices before granting access. Furthermore, advancements in quantum computing pose both challenges and opportunities for encryption technologies, necessitating the development of quantum-resistant protocols. The integration of AI and predictive analytics in security measures is likely to become more prevalent, enhancing real-time threat detection and response capabilities. These trends highlight the dynamic nature of secure data access protocols, necessitating continuous adaptation to address emerging challenges.
The future of secure data access protocols involves embracing cutting-edge technologies to stay ahead of potential threats. The advent of quantum computing highlights the need for quantum-proof encryption standards. Meanwhile, decentralized models like blockchain are gaining traction for their transparent and immutable properties. These innovations promise enhanced security, but also require proactive adaptation. Successful implementation of secure data access protocols in the future will rely heavily on the agility with which organizations can integrate these emerging technologies and reconfigure protocols to meet enhanced security demands.