In the contemporary digital era, the importance of secure user identity management cannot be overstated. As digital interactions proliferate, ensuring the integrity and confidentiality of user identities has become a paramount concern for organizations across the globe. Secure user identity management not only safeguards personal data but also fortifies trust in digital systems. This article will explore the various facets of secure user identity management, emphasizing its integral role in modern cybersecurity.
Understanding Secure User Identity Management
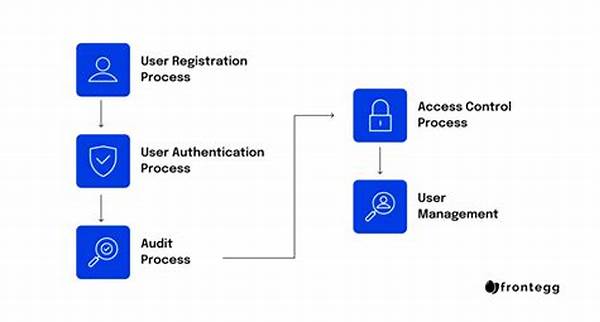
Secure user identity management involves a comprehensive framework of policies and technologies designed to protect and manage digital identities. The primary objective is to authenticate users accurately while safeguarding their personal information against unauthorized access and malicious activities. Moreover, secure user identity management ensures compliance with regulatory requirements and enhances the overall security posture of an organization.
In implementing secure user identity management systems, it is crucial to adopt multi-factor authentication, encryption protocols, and continuous monitoring practices. These measures collectively bolster the defense mechanisms against identity theft, data breaches, and other cyber threats. As technology evolves, secure user identity management must also adapt to emerging challenges, incorporating advanced analytics and machine learning to predict and mitigate potential vulnerabilities. The deployment of secure user identity management solutions ultimately fosters a safer digital environment for both individuals and organizations.
Components of Secure User Identity Management
1. Authentication Protocols: At the core of secure user identity management lies robust authentication protocols that verify the legitimacy of user identities using multiple factors such as passwords, biometrics, and security tokens.
2. Access Controls: Implementing stringent access controls ensures that only authorized individuals can access sensitive information, thereby strengthening secure user identity management frameworks.
3. Encryption Techniques: Protecting data in transit and at rest through encryption is vital for secure user identity management, preventing unauthorized interception or breach.
4. Continuous Monitoring: Ongoing observation of user activities aids in identifying anomalies and potential security threats, reinforcing secure user identity management practices.
5. Regulatory Compliance: Adhering to international and local regulations ensures that secure user identity management frameworks are legally sound and up-to-date.
Best Practices in Secure User Identity Management
Effective secure user identity management necessitates the adoption of best practices tailored to an organization’s specific needs. At the forefront is the need to implement strong password policies combined with multifactor authentication to balance security with user convenience. Regular training programs for employees and system users are paramount to foster awareness about potential security threats and the importance of adhering to established protocols.
Equipped with advanced technologies such as artificial intelligence and machine learning, organizations can swiftly detect and respond to suspicious activities, thereby enhancing the resilience of secure user identity management frameworks. Additionally, developing incident response strategies and conducting regular audits are instrumental in identifying vulnerabilities and ensuring continuous improvement of identity management systems. Implementing these best practices not only fortifies defense mechanisms but also engenders trust among users, reinforcing the reputation and credibility of an organization.
Challenges in Secure User Identity Management
Secure user identity management faces numerous challenges in the evolving digital landscape. One significant challenge is the sophisticated nature of cyber-attacks, which demands highly advanced security measures to thwart unauthorized access. Furthermore, maintaining user convenience while ensuring stringent security protocols remains a delicate balance for organizations.
Additionally, the proliferation of Internet of Things (IoT) devices complicates secure user identity management efforts due to the increased number of endpoints and potential vulnerabilities within a network. Privacy concerns and evolving regulatory requirements also pose challenges that necessitate continuous adaptation of identity management strategies. Addressing these challenges requires a proactive approach and a deep commitment to research and development in the field of secure user identity management.
The Role of Technology in Secure User Identity Management
Technological advancements play a pivotal role in enhancing secure user identity management systems. Implementation of biometrics, blockchain technology, and AI-driven analytics are among the innovative solutions that have revolutionized identity management. Biometrics provides a highly secure form of authentication by leveraging unique physical characteristics such as fingerprints and facial recognition.
Blockchain technology offers decentralized and tamper-proof records, ensuring the integrity of identity data. Meanwhile, AI-driven analytics can identify patterns and detect anomalies in real-time, significantly boosting the effectiveness of secure user identity management strategies. The integration of these technologies into identity management systems enhances security, scalability, and adaptability, enabling organizations to stay ahead in the ongoing battle against cyber threats.
Future Trends in Secure User Identity Management
As the digital domain continues to evolve, secure user identity management will witness transformative trends reshaping its landscape. The adoption of decentralized identity systems will gain traction, offering users greater control over their personal information while reducing reliance on centralized authorities. Behavioral biometrics, which analyzes unique user behaviors for authentication, is expected to complement existing authentication methods, providing an additional layer of security.
Furthermore, the integration of advanced machine learning algorithms will enable predictive analytics, allowing for proactive identity threat detection and response. Embracing these trends will be crucial for organizations seeking to maintain a robust secure user identity management framework amidst the ever-changing technological environment.
Summary of Secure User Identity Management
In summary, secure user identity management is a cornerstone in today’s digital infrastructure, integral to protecting sensitive information and maintaining user trust. By implementing comprehensive identity management strategies, organizations can effectively mitigate risks associated with identity theft and unauthorized access. The deployment of advanced authentication mechanisms, along with continuous monitoring, is essential to sustaining robust secure user identity management systems.
As challenges in the digital landscape intensify, organizations must remain agile, integrating innovative technologies and best practices to fortify their identity management frameworks. Looking towards the future, the evolution of secure user identity management will likely involve greater decentralization and the incorporation of AI-driven analytics, ensuring resilience against ever-evolving cyber threats. With a dedicated approach to security, organizations can provide users with confidence in their digital interactions, solidifying the foundation for a secure and trustworthy digital future.