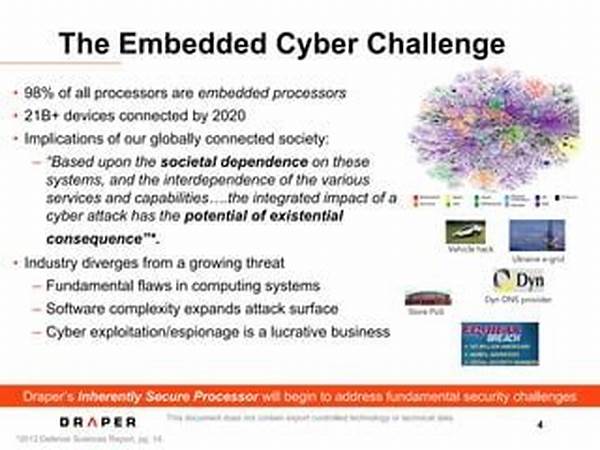
Addressing espionage challenges requires meticulous planning and deployment of well-considered solutions. In a world with heightened security risks, organizations and governments must be vigilant in implementing protective measures to safeguard sensitive information and infrastructure. Identifying and rectifying vulnerabilities is essential to preventing unauthorized access and potential threats. Below, we explore various strategic solutions to address espionage challenges, aiming to enhance security protocols and safeguard national and organizational interests.
Understanding Espionage Challenges
Espionage, both in the form of corporate and state-sponsored activities, presents significant threats to national security and organizational integrity. The advent of sophisticated technology has increased the capability and reach of those who conduct espionage, thus demanding equally advanced countermeasures. Solutions to address espionage challenges begin with recognizing these modern threats, which include cyber intrusions and insider threats, and then developing comprehensive strategies that incorporate both technological and human aspects of security. This dual approach ensures that defenses evolve in tandem with emerging threats, safeguarding critical assets from potential breaches.
Organizations must invest in continuous research and development to stay ahead of sophisticated espionage techniques. By harnessing the latest technological advancements, entities can create robust barriers against espionage attempts. However, technological solutions alone are insufficient. Cultivating a culture of security awareness among employees is equally imperative, as human error often presents a critical vulnerability. Ongoing training and stringent access controls are vital components of an effective strategy, each element reinforcing the other to create a formidable line of defense. Consequently, the adoption of these multifaceted solutions to address espionage challenges builds resilience against a broad spectrum of security threats.
Strategic Technological Solutions
1. Encryption Technologies: Implementing advanced encryption methods is a fundamental solution to address espionage challenges. Encryption protects sensitive data from unauthorized access during transmission and storage, ensuring confidentiality and integrity.
2. Intrusion Detection Systems: Deploying sophisticated intrusion detection systems is crucial. These systems monitor, detect, and respond to unauthorized network activities, thereby providing essential security insights that contribute to solutions to address espionage challenges.
3. Multi-Factor Authentication: Utilizing multi-factor authentication adds an additional layer of security, making it more difficult for unauthorized individuals to access protected systems and data, a vital part of solutions to address espionage challenges.
4. Regular Security Audits: Conducting regular security audits and vulnerability assessments ensures that systems remain robust against espionage threats. These audits are instrumental in identifying areas needing improvement within solutions to address espionage challenges.
5. Advanced Threat Intelligence: Leveraging threat intelligence platforms provides organizations with real-time data on potential espionage threats. This empowers them to implement proactive solutions to address espionage challenges effectively and efficiently.
Human Element Considerations
While technology plays a pivotal role in countering espionage, the human element cannot be overlooked. Experience shows that human oversight is often the weakest link in the safeguard chain. Educating employees on the nuances of espionage tactics and instilling a culture of vigilance can substantially mitigate risks. Developing policies that mandate security training for all personnel, regardless of their level or function, is a critical step toward comprehensive solutions to address espionage challenges.
Furthermore, establishing a well-structured reporting system encourages employees to report suspicious activities without fear of repercussions. Ensuring that these channels are effective and confidential contributes to a cohesive defense mechanism. Regular drills and simulations can further enforce an organization’s readiness to respond to potential espionage incidents swiftly and effectively. Therefore, integrating human considerations into solutions to address espionage challenges fortifies organizational defenses holistically.
Organizational Policy Development
To bolster defenses against espionage, organizations need to enact stringent policies. A clear and enforceable policy framework serves as a deterrent to potential espionage activities. Solutions to address espionage challenges must include well-drafted policies that define acceptable behavior and specify repercussions for violations.
These policies should also encompass guidelines for handling classified information, outlining measures for its protection and specifying protocols for its disclosure. A well-drafted policy acts as a bedrock for effective solutions to address espionage challenges by establishing a foundation for consistent security practices across the organization.
International Collaboration
Enhancing solutions to address espionage challenges also requires international cooperation. Espionage transcends borders, and a unified global effort can significantly enhance the effectiveness of countermeasures. By engaging in dialogue and sharing intelligence, countries can collectively develop more robust strategies to deal with this growing threat. International treaties and agreements play a vital role in establishing norms and frameworks for cooperation and information exchange.
Collaborating with international partners promotes the exchange of best practices, which is invaluable for crafting effective solutions to address espionage challenges. These collaborative efforts can lead to technological advancements and policy innovations that provide comprehensive protections across various domains. Therefore, a cohesive international strategy is paramount for addressing the multifaceted nature of espionage effectively.
Future Outlook on Solutions
As technology continues to advance, so too will the methods employed by those engaging in espionage. Consequently, staying ahead of potential threats necessitates continuous innovation and adaptation. Projects focused on artificial intelligence and machine learning hold promise in enhancing detection capabilities, thereby contributing to effective solutions to address espionage challenges.
Moreover, increasing public awareness regarding the importance of cybersecurity can aid in creating a more informed population that contributes to overall security efforts. Encouraging educational programs focused on digital literacy and cybersecurity fundamentals can further enhance societal resilience against espionage threats. Thus, solutions to address espionage challenges must evolve alongside technological progress to remain effective and relevant.
Summary
In summary, the intricate nature of espionage necessitates a multifaceted approach that combines technological, human, and policy-driven solutions to address espionage challenges. Advanced encryption, intrusion detection systems, and multi-factor authentication form the backbone of technological defenses, while continuous training and effective reporting systems bolster the human element. Meanwhile, organizational policies and international collaboration create a supportive framework for these initiatives, enhancing their efficacy.
To sustain these efforts, organizations and nations must remain vigilant and adaptive, continuously evaluating and enhancing their security strategies to align with emerging threats. The adoption of innovative technologies and international cooperation is imperative to ensure comprehensive security. As the landscape of espionage evolves, solutions to address espionage challenges must also transform, ensuring that sensitive information and infrastructure remain secure against unauthorized access and manipulation.