In the contemporary digital landscape, safeguarding information and infrastructure from threats has become paramount. The proliferation of cyber threats necessitates the implementation of robust threat detection and response systems to mitigate potential risks. These systems play a crucial role in identifying, analyzing, and neutralizing threats before they can inflict significant harm on an organization’s assets. As cybercriminals grow more sophisticated, the adoption of advanced threat detection and response systems becomes ever more essential, offering organizations a proactive means of defense against cyber adversaries.
The Importance of Threat Detection and Response Systems
Threat detection and response systems are pivotal in maintaining the security integrity of an organization. These systems are designed to detect potential threats in real-time and initiate appropriate responses to neutralize them. By leveraging advanced analytics, machine learning, and automation, threat detection and response systems are able to identify threats with high accuracy, thus reducing the probability of false positives. Furthermore, these systems provide comprehensive insights into threat patterns, enabling organizations to fine-tune their security measures and strategies. Such capabilities not only defend against immediate threats but also help build a resilient security architecture capable of withstanding future attacks. As the digital threat landscape evolves, the deployment of effective threat detection and response systems becomes an integral component of an organization’s cybersecurity strategy.
Components of Effective Threat Detection and Response Systems
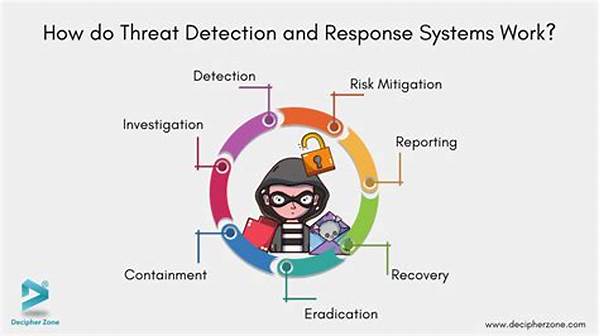
1. Real-Time Monitoring and Alerts: Threat detection and response systems constantly monitor networks for suspicious activities and immediately alert security teams.
2. Machine Learning Integration: By incorporating machine learning, systems improve threat detection capabilities, adapting to emerging threats.
3. Automated Response Mechanisms: These systems provide automated responses to mitigate threats instantly.
4. Threat Intelligence Collaboration: Integration with threat intelligence platforms ensures updated information on new and evolving threats.
5. Comprehensive Reporting and Analysis: Detailed reports and analytics assist in understanding threat patterns and planning future defenses.
Implementation Challenges of Threat Detection and Response Systems
Adopting threat detection and response systems is fraught with challenges, despite their fundamental importance in securing digital assets. One significant challenge is the integration of these systems with existing IT infrastructure. Organizations often have a complex array of legacy systems and disparate technologies, making seamless integration a difficult task. This complexity necessitates careful planning and execution to ensure that the threat detection and response systems function optimally across varied environments. Furthermore, as organizations scale, they must ensure these systems can handle increased volumes of data without compromising on performance or accuracy.
Additionally, the rapid evolution of cyber threats presents another formidable challenge. Threat detection and response systems must constantly evolve to detect and counteract new and sophisticated forms of attack. This requires continuous updates and enhancements, demanding significant resources and investment. Organizations must also contend with the scarcity of skilled cybersecurity professionals capable of managing and optimizing these sophisticated systems. Overcoming these challenges is critical for organizations endeavoring to build resilient cybersecurity defenses through effective threat detection and response systems.
Benefits of Threat Detection and Response Systems
1. Enhanced Security Posture: They bolster organizational defenses against cyber adversaries by providing real-time insights and responses.
2. Reduced Incidents of Data Breach: These systems mitigate the risk of data breaches and the associated reputational and financial repercussions.
3. Proactive Threat Management: They allow for proactive management of potential threats before actual incidents occur.
4. Improved Compliance: Threat detection and response systems help organizations maintain compliance with industry regulations.
5. Cost-Effectiveness: By preventing breaches, they reduce the potential costs associated with recovery and remediation.
6. Operational Continuity: Effective systems ensure business operations continue without disruption from cyber threats.
7. Real-Time Protection: Continuous monitoring provides protection against threats as they happen.
8. Better Resource Allocation: Automation allows for better allocation of human resources to strategic activities.
9. Scalability: Adaptable to growing organizational needs and increasing threat volumes.
10. Comprehensive Threat Understanding: They provide insights that sharpen the organization’s understanding of the threat landscape.
Evolution of Threat Detection and Response Systems
The evolution of threat detection and response systems reflects the dynamic nature of cyber threats. Initially, cybersecurity primarily relied on signature-based detection methods, which were effective for known threats but inadequate for emerging and unknown attacks. Over time, the advent of advanced machine learning and artificial intelligence technologies revolutionized threat detection and response systems. These technologies enable systems to identify and respond to new, elusive threats by analyzing patterns and behaviors rather than relying solely on signatures.
In addition, the rise of cloud computing and the ubiquitous nature of IoT devices necessitate more robust and flexible threat detection and response systems. Modern systems must handle diverse data sources and provide protection across widely distributed environments. As these systems continue to develop, they must incorporate innovative technologies and methodologies to address the ever-evolving threat landscape effectively. This evolution underscores the necessity for organizations to remain vigilant and ensure their systems are up-to-date with the latest advancements in threat detection and response capabilities.
Future Trends in Threat Detection and Response Systems
As organizations continue to embrace digital transformation, future trends in threat detection and response systems will focus on enhancing their efficacy and scope. Artificial Intelligence will become even more integral, with systems leveraging AI for smarter threat identification and autonomous response strategies. Furthermore, the integration of threat detection and response systems with broader cyber-defense ecosystems will become commonplace, enabling seamless flow of information and heightened overall security.
The emphasis on user-centric security solutions will also grow, making threat detection and response systems more intuitive and accessible for security teams of varying expertise levels. As the sophistication of cyber threats increases, so will the demand for systems capable of cross-platform and cross-environment adaptation, ensuring robust protection regardless of where data resides. Consequently, organizations must remain proactive, continually pursuing upgrades and innovations in threat detection and response systems to maintain their security postures effectively.
Conclusion
In conclusion, threat detection and response systems are an indispensable component of modern cybersecurity frameworks. These systems provide real-time protection, ensuring incidents are detected and mitigated promptly. The robust integration of machine learning, automation, and advanced analytics not only enhances threat detection capabilities but also empowers organizations to effectively manage and predict possible threats. Consequently, threat detection and response systems do not merely act as passive defenders against intrusions; they actively contribute to the strategic bolstering of an organization’s cyber defense posture.
As cyber threats continue to evolve and diversify, organizations must recognize the necessity of investing in and continuously upgrading their threat detection and response systems. The future of cybersecurity will undeniably rely on these advanced systems to ensure the confidentiality, integrity, and availability of digital assets. As such, organizations are called upon to remain at the forefront of technological advancements, adapting their strategies to leverage the benefits of cutting-edge threat detection and response systems in an increasingly complex digital world.